الوحدة 10
تمرين "التقط العلم"(Catch The Flag)
آخر تحديث في: 16 يناير 2025
GitHub تعديل هذه الصفحة علىالوحدة 10
آخر تحديث في: 16 يناير 2025
GitHub تعديل هذه الصفحة علىلقد صممنا أيضاً تمرين التقاط العلم حيث يمكن للمتعلمين تحليل رسالة بريد إلكتروني للتصيد الاحتيالي والبنية التحتية التي ترتبط بها. يمكن استخدام التمرين كتدريب إضافي أو تمرين إضافي للتحقق من المهارات، ويمكن الاطلاع عليه هنا.
تجلس/ تجلسين في غرفة الأخبار الصحفية حيث تعمل/ تعملين كمسؤول/ مسؤولة عن تكنولوجيا المعلومات، وتجلس/ تجلسين مركز/مركزة تماماً على واجباتك محاط/ محاطة بشاشات مختلفة. يهرع إليك زميلتك علياء من قسم المحاسبة وعلى وجهها نظرة قلق، وتخبرك أنه أرسل لها رسالة بريد إلكتروني يدّعي أنه من PayPal يحثها على اتخاذ إجراء فوري بسبب نشاط مشبوه في الحساب. تعتمد المؤسسة الصحفية على PayPal لمعالجة مدفوعات الاشتراكات. يثار اهتمامك على الفور لأنك/أنكي تدرك/تدركين احتمال وجود هجوم خبيث، وتبدأ/تبدئين في إجراء تحقيق.
يستخدم هذا النشاط نموذج البريد الإلكتروني والصفحة المقصودة اللازمة لهذا النشاط. قم بتنزيل الملف هنا CTF Materials
هناك عدة طرق لعرض شكل البريد الإلكتروني على المستلم. الطريقة الأكثر وضوحًا هي فتح الملف في عميل البريد، وهو ما قمنا به في الأمثلة أدناه. ولكن في سياق التهديد المستهدف، قد تكون هذه فكرة سيئة، في حالة احتواء الملف على نصوص برمجية يمكنها استغلال عملاء البريد الإلكتروني، أو جمع معلومات عن الجهاز، أو تحميل موارد خارجية (مثل الصور/بكسلات التتبع) التي تكشف عنوان IP الخاص بك للمهاجم. في حالة هذه الإرشادات، من الآمن فتح ملف EML في عميل البريد الإلكتروني الخاص بك، ولكن للعمل المباشر، فكر في بعض البدائل:
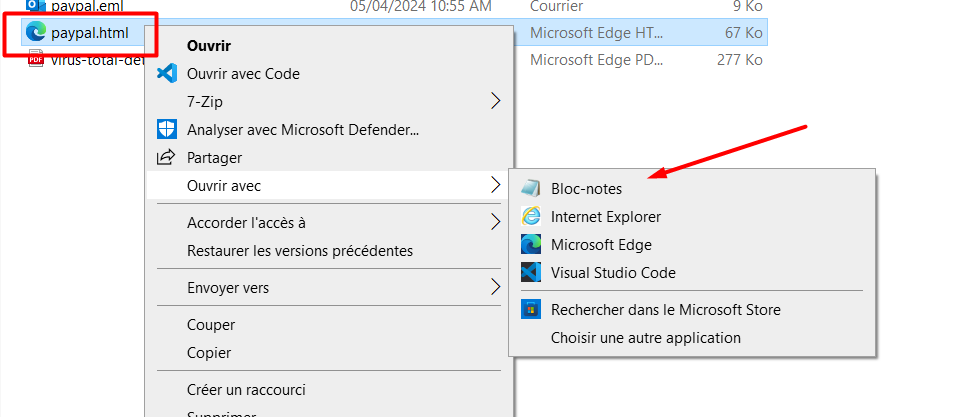
في هذه الإرشادات التفصيلية سنقوم فقط بفتح البريد الإلكتروني (paypal.eml) في برنامج بريد إلكتروني
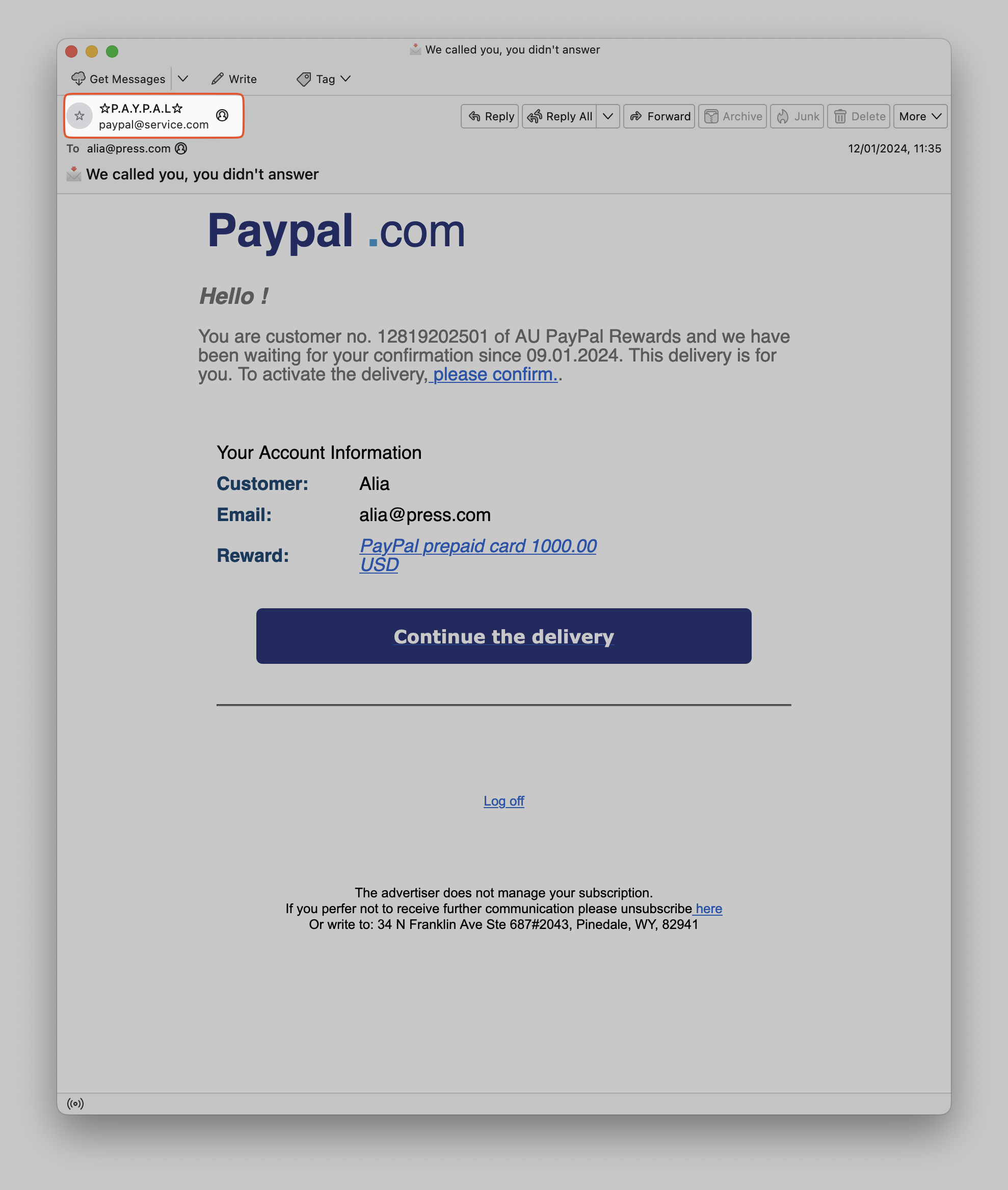
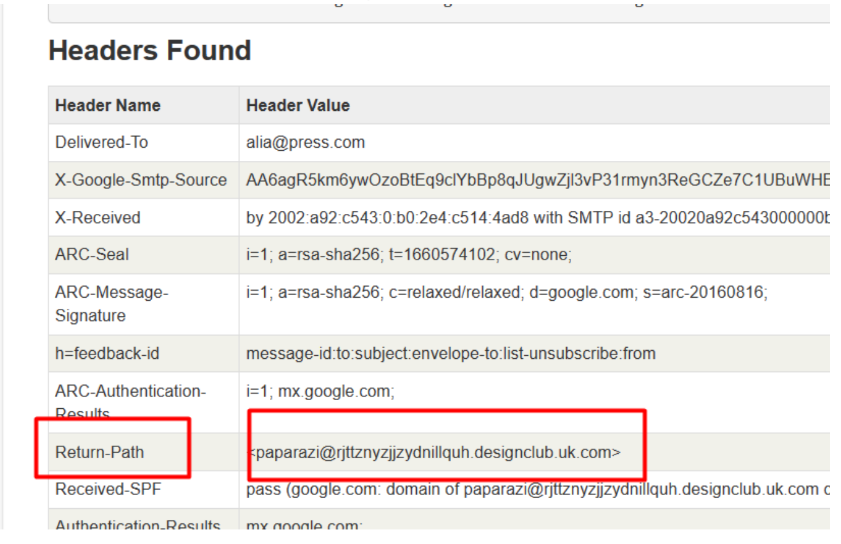
عندما ننظر إلى البريد الإلكتروني، نرى عنوان مرسل البريد الإلكتروني
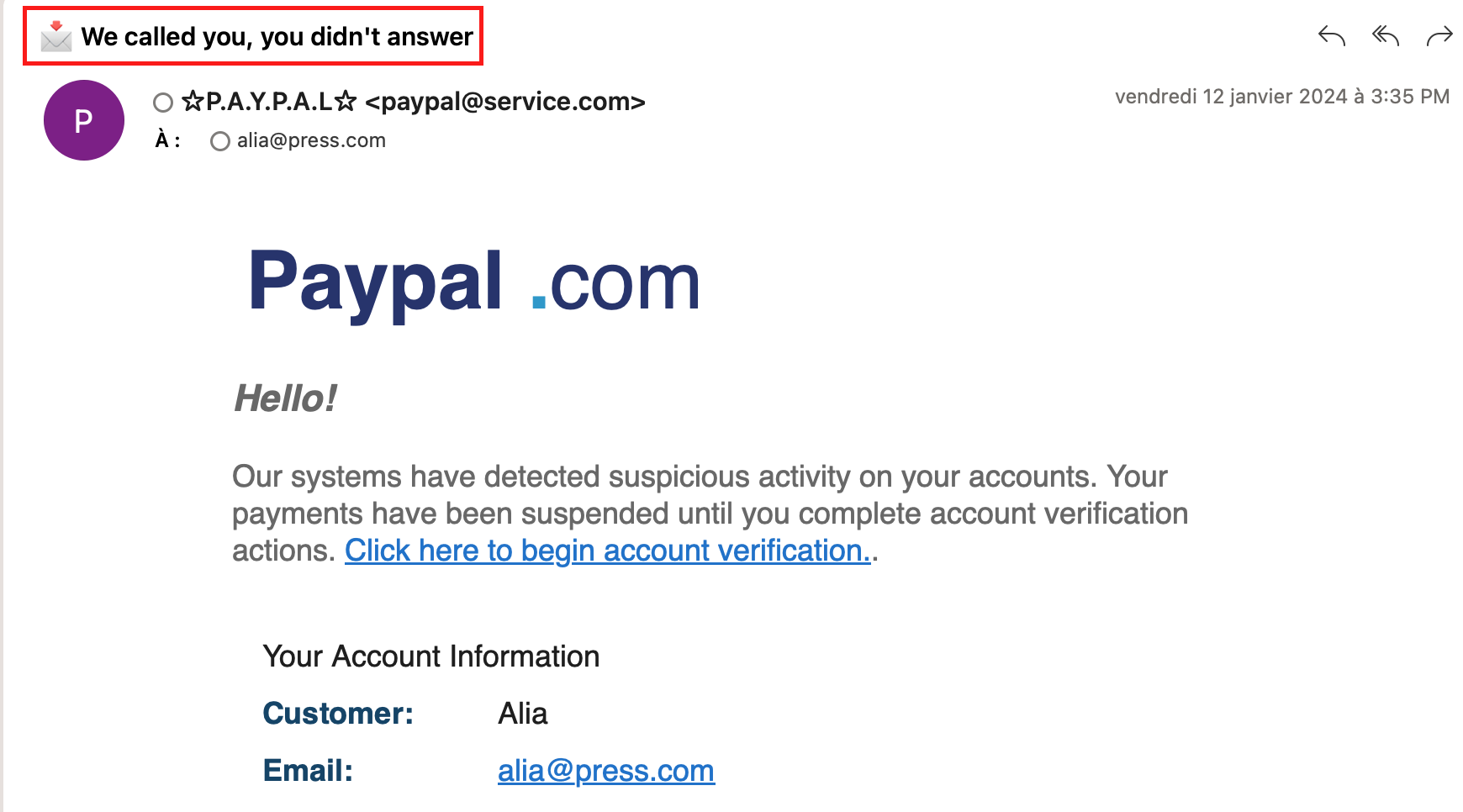
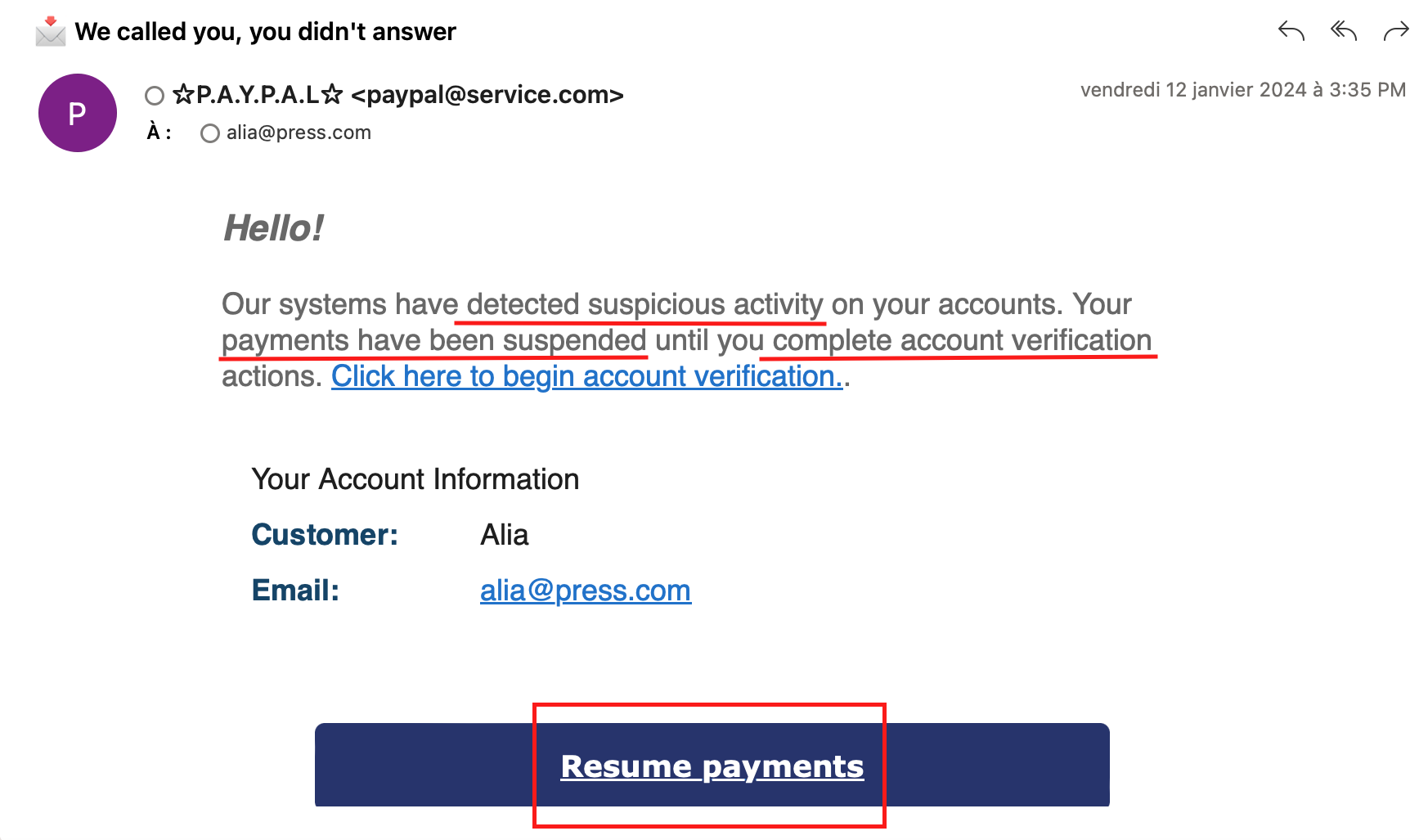
فيما يلي بعض النقاط الرئيسية التي يجب الانتباه إليها في رسائل التصيد الاحتيالي:
يمكنك إلغاء تشفير رابط في محرر النصوص. سنستخدم هناCyberChef لإلغاء تشفير عنوان URL كما سنستخدم CyberChef لخطوات أخرى أيضًا. CyberChef هو تطبيق ويب يحتوي على عدد كبير من الوظائف التي يمكن أن تساعدك في تحليل البيانات المتعلقة بالأمان. إليك مقدمة موجزة جداً عن تصميمه ووظائفه.
كجزء من هذا التمرين، استخدم CyberChef وقم بإلغاء رابط “please confirm” من البريد الإلكتروني المرفق
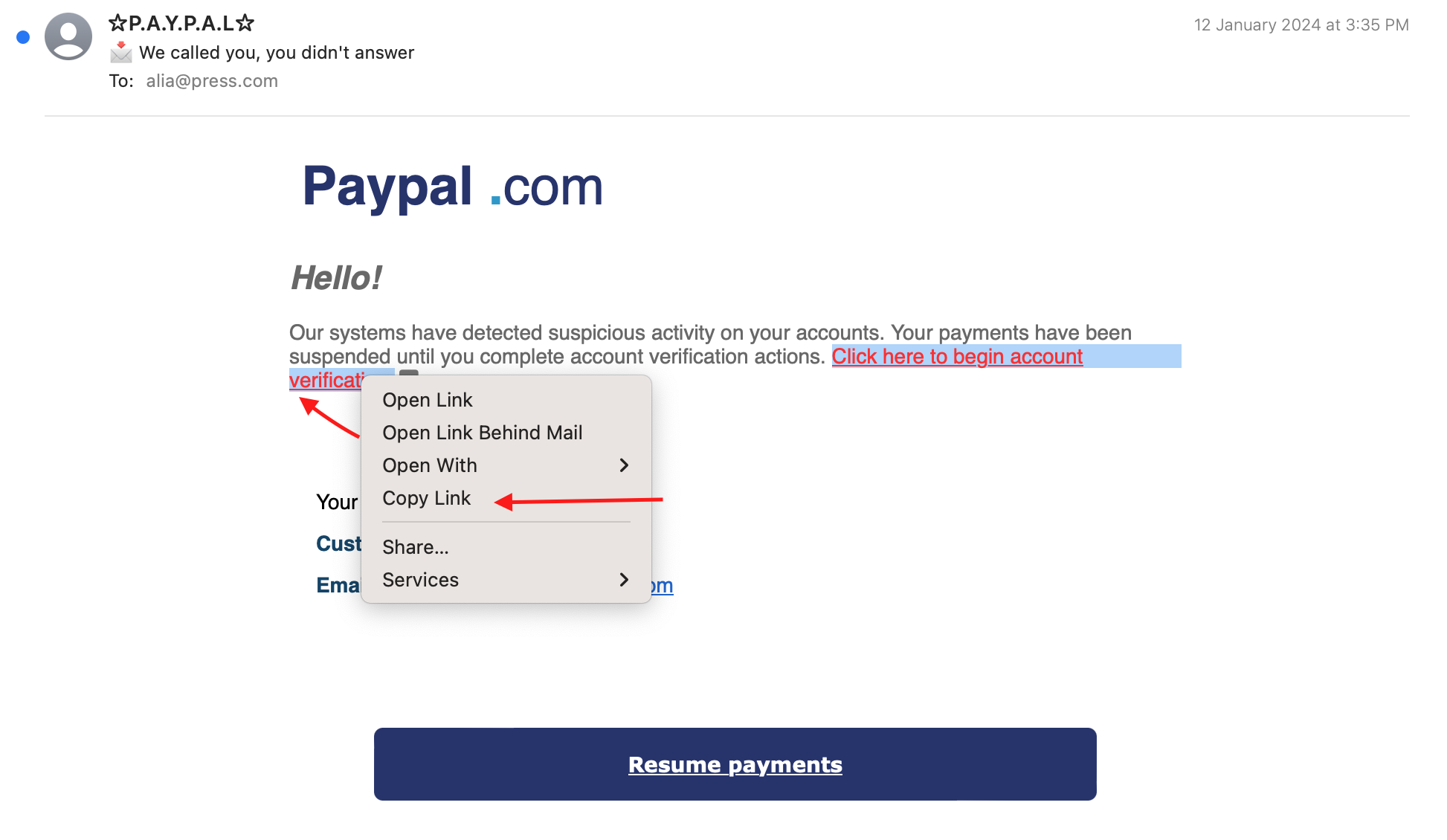 أولاً، نقوم بنسخ الرابط التشعبي (hyperlink) من البريد الإلكتروني.
أولاً، نقوم بنسخ الرابط التشعبي (hyperlink) من البريد الإلكتروني.
 بعد ذلك، نأخذ مدخل “عنوان URL الخاص بـ “Defang URL” من CyberChef ونسحبه إلى قسم “Recipe”
بعد ذلك، نأخذ مدخل “عنوان URL الخاص بـ “Defang URL” من CyberChef ونسحبه إلى قسم “Recipe”
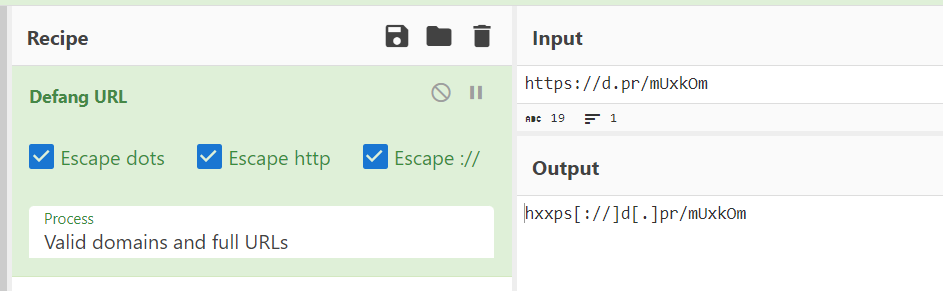
بمجرد أن نقوم بلصق عنوان URL في قسم الإدخال في CyberChef، سيُخرج تلقائيًا نسخة غير منقوصة منه.
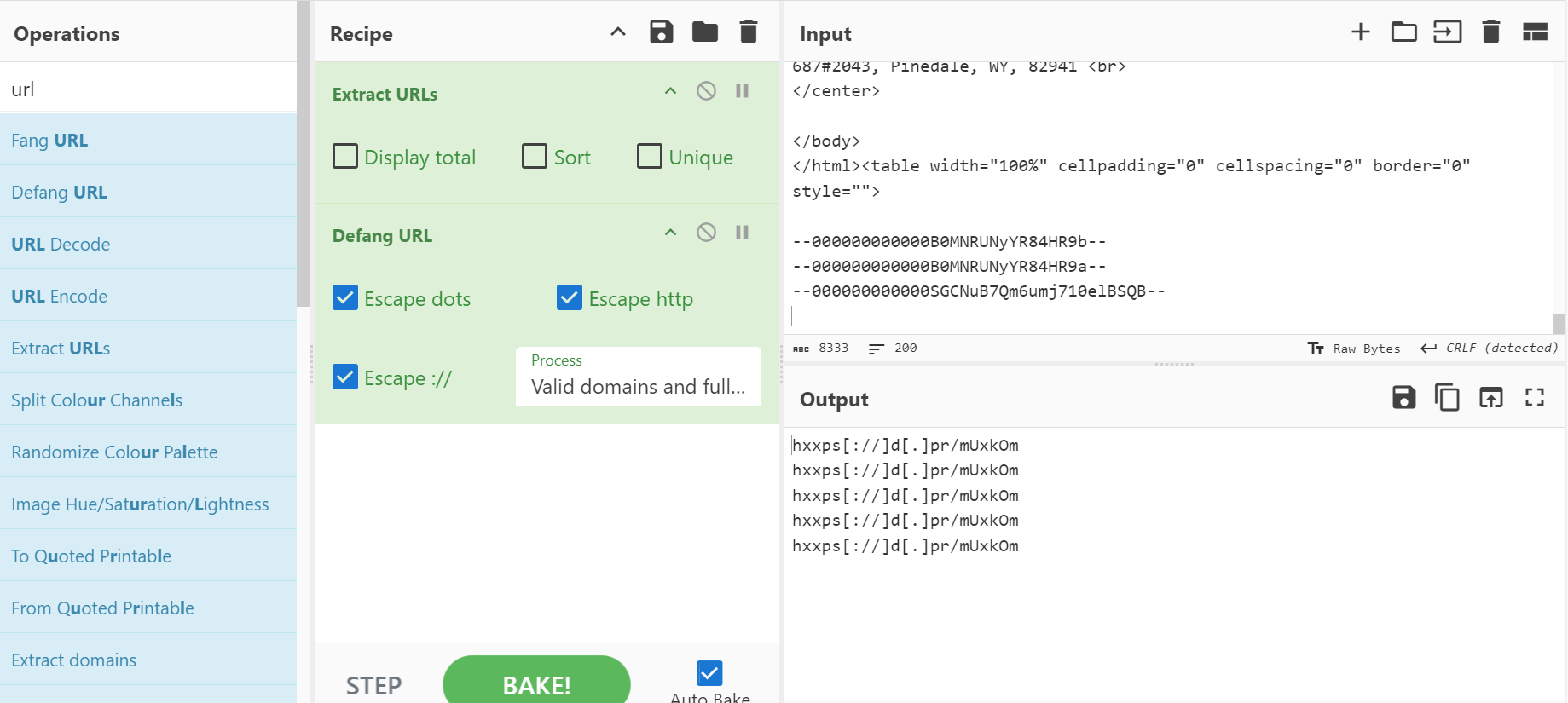
يمكنك استخدام “وصفة” - أو سلسلة من الخطوات المتصلة - في CyberChef لإجراء تحليل أكثر تعقيدًا. للحصول على جميع عناوين URL الموجودة في الرسالة وإلغاء تشفيرها، كل ما عليك فعله هو تشغيل وصفة باستخدام “استخراج عناوين URL” و “إلغاء تشفير عناوين URL” ولصق المحتوى الكامل للبريد الإلكتروني (المنسوخ من محرر نص عادي) كمدخلات. إذا كنت ستضع علامة اختيار “فريد” ضمن خانة الاختيار “فريد” تحت “استخراج عناوين URL”، فسترى أن النتائج ستختلف عن تلك الموجودة في لقطة الشاشة، وستخرج عنوان URL واحد فقط، وهو نفس العنوان الذي قمت بإلغاء تحديده أعلاه. حقيقة أن هناك عنوان URL واحد فقط، يتكرر عدة مرات، داخل البريد الإلكتروني هو خبر رائع بالنسبة لنا - سيجعل تحليلنا أكثر وضوحًا.
فكر في الأمر كمفتش رقمي. يمكنك تحميل ملف أو توفير عنوان URL، ويقوم VirusTotal بفحصه باستخدام محركات مكافحة الفيروسات وأدوات فحص المواقع الإلكترونية من عشرات الشركات الأمنية المختلفة. كما يقوم أيضاً بإجراء بعض التحليلات الإضافية. يمنحك هذا نظرة عامة سريعة حول ما إذا كان الملف أو الموقع الإلكتروني من المحتمل أن يكون خبيثاً. إنها أداة قيّمة لمساعدتك في تحديد التهديدات المحتملة قبل فتح مرفق أو النقر على رابط. كما أنه يحتوي على بيانات وصفية حول الملفات التي قد تكون مفيدة. سنستخدم هنا سجل الإدخال لمعرفة متى تم رصد مؤشر ضار لأول مرة.
ابحث أيضًا في علامة التبويب “details” في VirusTotal، وابحث عن عنوان IP الذي يقدم الخدمة
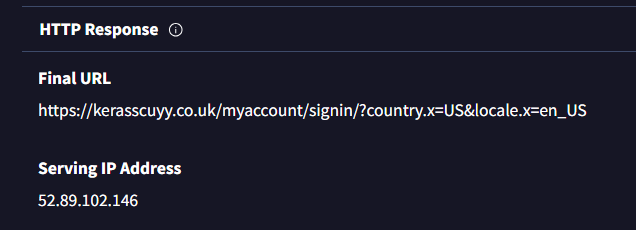
هنا نستخدم موقع whois لاستخراجها.
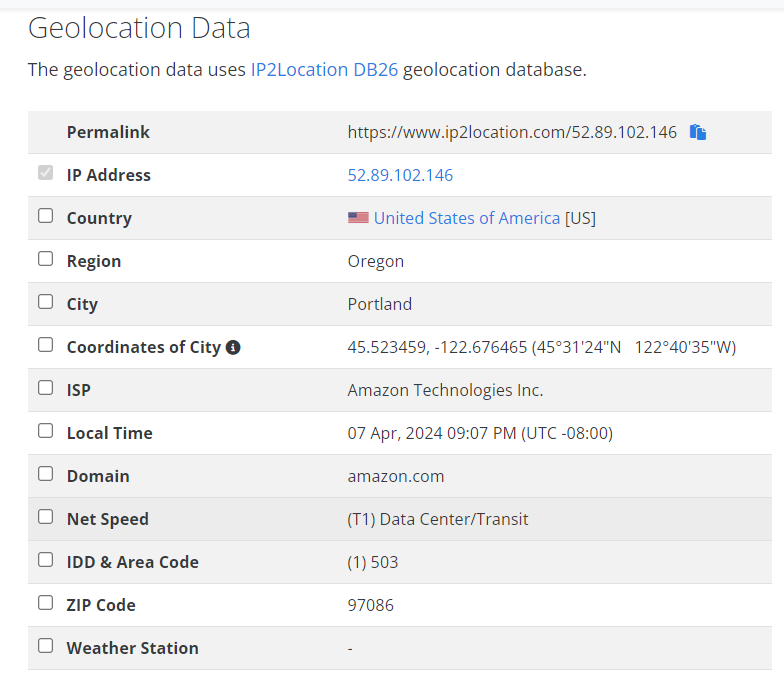
ترتبط عناوين IP بشكل عام بالمواقع الجغرافية، مثل المدن أو المقاطعات. هناك العديد من الخدمات عبر الإنترنت حيث يمكنك إدخال عنوان IP ومعرفة المزيد عن المكان الذي يُرجّح أن يكون موقعه. على الرغم من أن هذا النوع من الفحص ليس مثاليًا ويمكن أن يخطئ في بعض الأحيان، إلا أنه يمكن أن يكون جزءًا مهمًا من تحقيقات البنية التحتية الخبيثة. من المفيد مقارنة المعلومات التي تتلقاها من البحث عن هوز مع تلك التي تتلقاها من عمليات البحث عن موقع بروتوكول الإنترنت. قد تعلم أن عنوان بروتوكول الإنترنت الذي تحاول التحري عنه ينتمي إلى مزود شبكة افتراضية خاصة أو شركة تقنية كبيرة مثل جوجل - إذا كان هذا هو الحال، فلن تتعلم الكثير من تلك التحقيقات؛ من المحتمل أن يتوافق موقع بروتوكول الإنترنت مع إحدى مزارع خوادم تلك الشركات وقد لا يكون له علاقة كبيرة بموقع الشخص أو الكيان الذي تحاول التحري عنه.
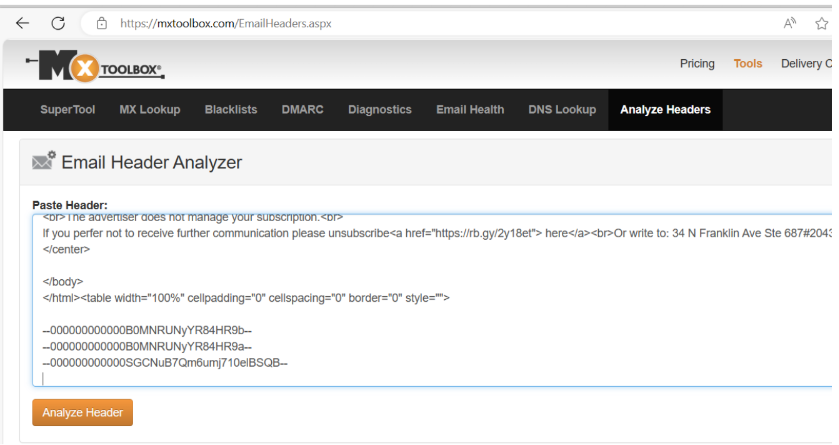
First, open the email using a plain text editor of your choice and copy its content. Then, paste them into the MxToolbox’s “Analyze Headers” tool
Once you press “Analyze Header”, you can see the return path
انتقل إلى الملف “mx-toolbox-oolbox-header-ananalysis”، وانظر إلى قسم معلومات الترحيل.
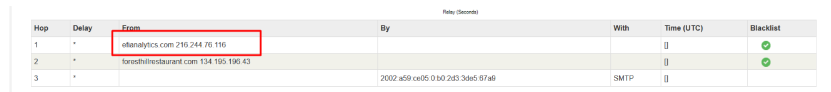 عنوان خادم البريد الإلكتروني
عنوان خادم البريد الإلكتروني
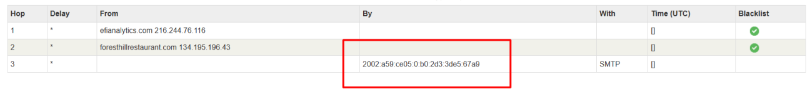
First hop: efianalytics.com 216.244.76.116
SMTP: 2002:a59:ce05:0:b0:2d3:3de5:67a9
في هذا التمرين، ستواجه في هذا التمرين سلسلة نصية مشفرة في Base64. Base64 هي تقنية لتحويل النص لها العديد من الأغراض، لكنها في هذه الحالة تهدف إلى تشويش “obfuscation” سلسلة نصية: السلسلة لا تزال موجودة، لكنها محفوظة بطريقة لا يمكن رصدها بسهولة بالعين البشرية أو بالبحث البسيط عن النص. إذا كانت هذه هي المرة الأولى التي تصادف فيها Base64 في عملك، فمن المفيد أن تقرأ المزيد عنها وعن غيرها من صيغ التشويشa little more about it and other obfuscation formats . يحب مؤلفو البرمجيات الخبيثة تشويش بعض السلاسل النصية داخل برامجهم باستخدام تقنية مثل Base64 من أجل جعل تحليلها أكثر صعوبة. يستطيع CyberChef تشفير وفك تشفير نص Base64.
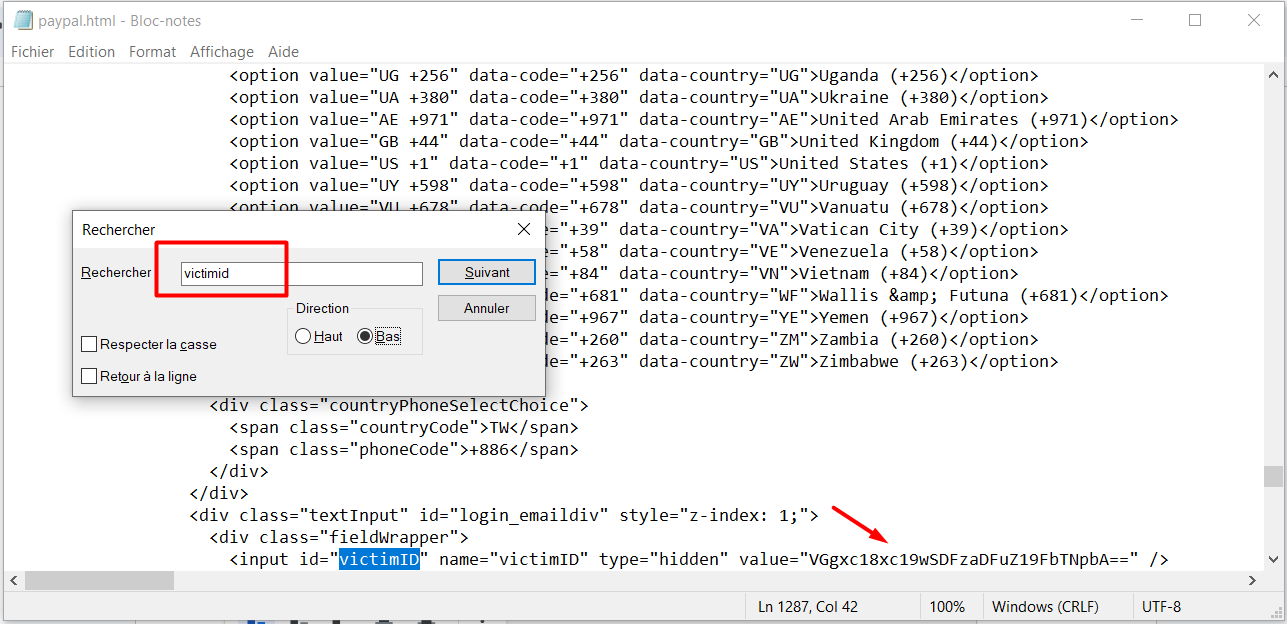
نفتح مرة أخرى الكود المرفق لصفحة التصيد الاحتيالي (.html)
نبحث عن معرّف الضحية victimID في الكود المصدري source code
ثم يمكننا لصق القيمة التي اكتشفناها في CyberChef. تحتوي الأداة على خاصية العصا السحرية “magic wand” التي تكتشف التشفير وتحوّله تلقائيًا - يمكننا استخدام ذلك!
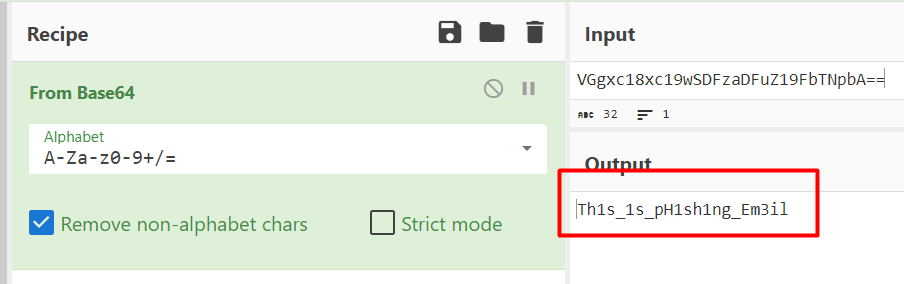
حسناً! اكتشفت العصا السحرية أن المدخلات مشفرة باستخدام Base64 وفكت تشفيرها تلقائيًا، مما أعطانا الإجابة!
Access Now helpline community documentation for responding to suspicious/phishing emails
FreeClient Receives a Suspicious/Phishing Email
List of all DNS record types
FreeIncludes (almost?) all DNS record types.
Amnesty reports on phishing campaigns
FreeA list of examples of how a targeted phishing campaign against human right defenders, activists and journalists looks
تهانينا على إنهائك الوحدة 10!
حدد خانة الاختيار لتأكيد إكمالك والمتابعة إلى الوحدة التالية.
تحديد الوحدة الحالية على أنها مكتملة وحفظ التقدم للمستخدم.
لقد أكملت جميع الوحدات في مسار التعلم هذا.