الوحدة 1
الإعداد
آخر تحديث في: 28 نوفمبر 2024
GitHub تعديل هذه الصفحة علىالوحدة 1
آخر تحديث في: 28 نوفمبر 2024
GitHub تعديل هذه الصفحة علىيتطلب الاختبار الفعّال لتطبيقات الويب للكشف عن الثغرات الأمنية أدوات متخصصة وهو ما يتطرق إليه هذا الموضوع الفرعي.
تُعدّ أهم هذه الأدوات هي خادم وكيل اعتراض سيسمح لك بالتفاعل مباشرة مع بيانات بروتوكول نقل النص التشعبي أثناء تدفقها ذهابًا وإيابًا بين متصفحك وخادم الويب المستهدف، وسيتيح لك هذا مراقبة البيانات التي تم تبادلها والتلاعب بها دون تدخل من متصفحك أو أي عناصر تحكم موجودة من جانب العميل.
هناك أدوات إضافية يمكنها اختبار مواقع الويب تلقائيًا لأنواع معينة من الثغرات، مما يمكن أن يؤدي إلى تسريع الاختبار وكشف بعض الثغرات الأمنية التي ربما تكون قد فاتتك.
أخيرًا هناك بعض الأدوات التي ستكون مطلوبة للأنشطة العملية في مسار التعلّم هذا.
بعد استكمال هذا الموضوع الفرعي، سيتم إعداد البرامج والحسابات للممارسين لإكمال بقية مسار التعلّم هذا ومعرفة كيفية استخدامها بما في ذلك البرامج وخدمة برمجية الحلول التالية:
هناك ثلاثة مناهج رئيسية لتقييم أمان تطبيقات الويب:
اختبار الصندوق الأبيض: نتمتع بالوصول الكامل إلى شفرة مصدر التطبيق وبنيته الأساسية ووثائقه، ويسمح هذا الوصول الشامل بإجراء فحص متعمق لتحديد الثغرات مما يتطلب مهارات في مراجعة التعليمات البرمجية المصدر وفهم منطق التطبيق، ويُعدّ الطريقة الأكثر شمولاً وأيضًا الأكثر استغراقًا للوقت.
اختبار الصندوق الأسود: نبدأ دون أي معرفة بالتطبيق مع التركيز على اكتشاف المعلومات من خلال التعداد، وهذا النهج شائع في برامج مكافآت كشف الأخطاء ويتطلب جهدًا كبيرًا في المراحل الأولية لتحديد الثغرات المحتملة.
اختبار الصندوق الرمادي: توفر لنا هذه الطريقة معلومات محدودة حول التطبيق مثل طرق المصادقة أو تفاصيل الإطار مما يوفر توازنًا بين التحليل المتعمّق والاستكشاف الخارجي.
يجري اختيار كل طريقة بناءً على السياق المحدد للتقييم بما في ذلك المعلومات المتاحة وأهداف المشاركة.
الأداة الأساسية المستخدمة في تقييمات أمان تطبيقات الويب هي خادم وكيل. اعتراض، وقد تكون على دراية بأنواع أخرى من الوكلاء مثل:
يأتي وكلاء الويب على الشبكة بين تطبيق الويب وخادم الويب ويؤثران على حركة مرور الشبكة هذه.
عادةً ما يجري ضبط وكلاء الويب ليكونوا إما وكلاء أماميين أو وكلاء عكسيين (وكيل شفاف). في حالة الوكيل الأمامي يجري تكوين المتصفح لاستخدام الخادم الوكيل بشكل صريح، ويقوم المتصفح بعدها بإرسال طلب اتصال إلى الوكيل ويطلب منه إعادة توجيه طلبه إلى الخادم الحقيقي. نظرًا لأن متصفح الويب يخبر الوكيل بالموقع الذي يحاول الاتصال به يمكن للوكلاء الأماميين إجراء اتصالات بالعديد من مواقع الويب الخلفية (الأصلية)، وهذا على النقيض من الوكلاء العكسيين (أدناه). لا يظهر الوكلاء العكسيون بشكل خادم وكيل للمتصفح ولكن بدلاً من ذلك يتظاهر بأنه الخادم نفسه، ويمكن أن تكون هذه ميزة للعملاء أو التطبيقات التي لا تدعم الخوادم الوكيلة. عادةً ما يكون إعداد وكيل عكسي أمرًا يتطلب مشاركة أكبر مقارنة بالوكيل الأمامي مع تكوين لكل موقع وتغييرات نظام أسماء المجالات. نظرًا لأن المتصفح لا يعرف أن الوكيل المعكوس هو خادم وكيل حتى، يمكن لكل وكيل عكسي أن يتصل فقط بموقع ويب واحد خلفي (الأصل).
أجل توضيح إضافي للوكلاء العكسيين، اطلع على هذا الدليل.
يعمل نوع الوكيل المستخدم لاختبار تطبيقات الويب بشكل شائع على ذات كمبيوتر متصفح الويب الخاص بالشخص الفاحص ولكن ليس هذا أمرًا مطلوبًا، وهذا هو نوع الوكيل الذي سنستخدمه في مسار التعلّم هذا. كما سيقوم أيضًا باعتراض بروتوكول أمان طبقة النقل وفك تشفير حركة مرور الشبكة. تُعدّ الميزة الرئيسية لهذه الوكلاء هي سماحها للمستخدم بمشاهدة رسم بياني لحركة مرور الشبكة بين المتصفح والخادم وإيقافها مؤقتًا وتعديلها يدويًا. على سبيل المثال إذا أرسل مجري الاختبار نموذجًا تسبب بقيام متصفحه بإرسال طلب بوست (POST) إلى الخادم، فسيسمح الوكيل للشخص الفاحص بمشاهدة الطلب الكامل وتعديله قبل إرساله فعليًا إلى الخادم. قد تحتوي خوادم الوكيل المختلفة على العديد من الميزات، مثل ميزات التعليمات البرمجة والأتمتة، وفهرسة الموقع، وأدوات للفحص الترجيحي لتطبيقات الويب تلقائيًا.
هناك وكيلان شائعان لاعتراض الويب يُستخدمان للتقييمات الأمنية وهما بيرب سويت من بورت سويغر وأداة زد أتاك بروكسي من سوفتوير سيكيوريتي بروجكت (Software Security Project أو اختصارًا SSP). بيرب سويت هو برنامج مدفوع يأتي مع إصدار مجتمع محدود الميزات في حين أن زد أتاك بروكسي مفتوح المصدر. تتوفر غالبية تمارين الممارسة في مسار التعلّم هذا من بورت سويغر لذلك يتم كتابتها مع وضع استخدام بيرب سويت في الاعتبار، ولكن يمكنك استخدام أي من الوكيلين أو كليهما. نوصي باستخدام بيرب سويت إصدار المجتمع لمعظم المواضيع الفرعية ولكن هناك موضوع فرعي مخصص لاستخدام أداة زد أتاك لعملية تلقائية لاختبار الأمان.
لبدء استخدام بيرب عليك أولًا تنزيله ثم قم بتثبيت التطبيق وفتحه. قبل البدء في استخدام بيرب، سيطلب منك تحديد مشروع وإجراء تكوين، وتتيح لك المشاريع تتبع تقدمك في اختبار موقع ما بين الجلسات ولكنها غير مدعومة في الإصدار المجاني لذلك ما عليك سوى تحديد “مشروع مؤقت”، ويمكنك أيضًا تحديد مجموعات مختلفة من التكوينات ولكن حاليًا اختر “استخدام الإعدادات الافتراضية لبيرب (Use Burp defaults)”.
سينقلك هذا إلى نافذة بيرب الرئيسية حيث ستستخدم علامتي التبويب الأساسيتين “الوكيل” و"الدخيل". في الوقت الحالي انتقل إلى علامة تبويب الوكيل وانقر على زر “فتح المتصفح”. سيؤدي هذا إلى فتح مثيل كروميوم (Chromium)الذي تم تكوينه بالكامل لاستخدام بيرب، تم تكوين هذا المتصفح المضمن لاستخدام بيرب كوكيل له وتم تغيير تكوين بروتوكول أمان طبقة النقل للسماح لبيرب باعتراض حركة المرور المشفرة. يمكنك استخدام مثيل المتصفح هذا لاختبار تطبيقات الويب أثناء استخدام المتصفح العادي للتصفح العام.
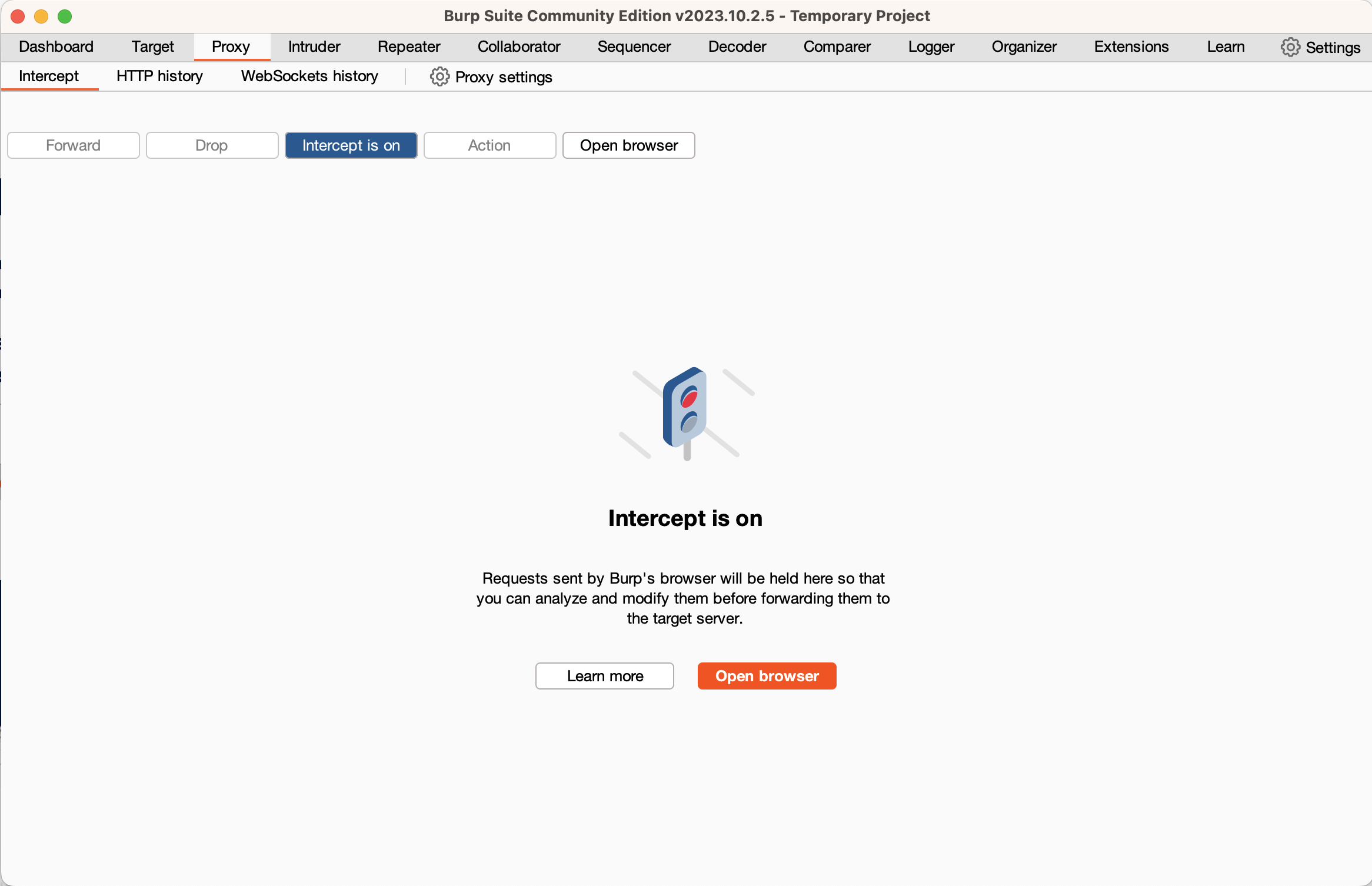
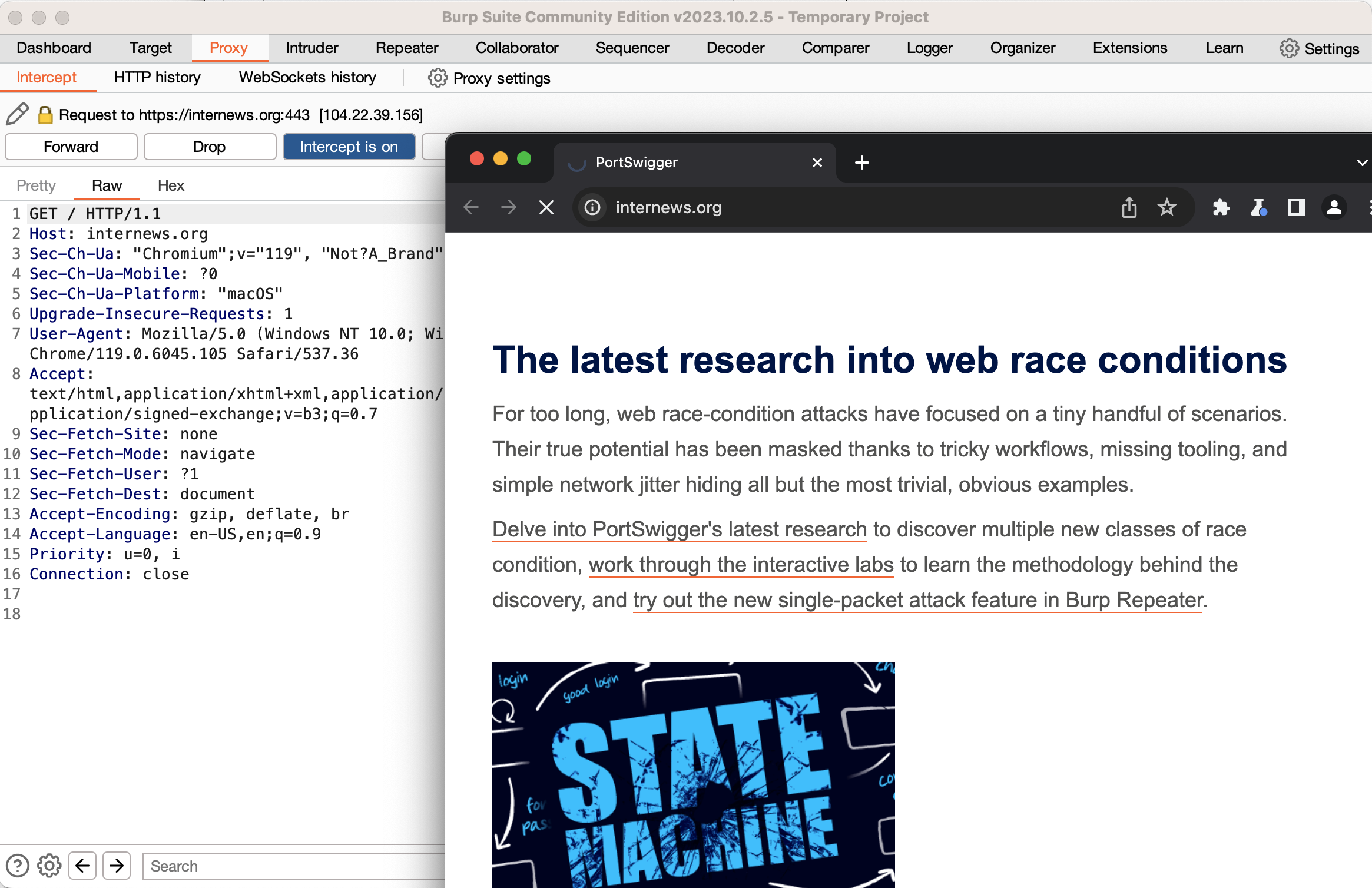
اكتب حاليًا عنوان موقع ويب يخص أي موقع في متصفح بيرب المضمن واضغط على إدخال، وستلاحظ أنه لا يحدث شيء في المتصفح. انتقل مرة أخرى إلى بيرب وسترى طلب بروتوكول نقل النص التشعبي الذي أرسله المتصفح وسيضيء زر يقول “الاعتراض قيد التشغيل”. ما حدث هو أن بيرب قد تلقى الطلب من متصفحك ولكنه لم يُعِد توجيهه إلى خادم الويب. بدلاً من ذلك يسمح لك بفحص الطلب وتعديله، ولكن في الوقت الحالي انقر على زر “تشغيل الاعتراض (intercept is on)” لإيقاف الاعتراض. وإذا نظرت إلى كروميوم المضمن في بيرب فسترى صفحة الويب محملة. انتقل مرة أخرى إلى بيرب وانقر على علامة التبويب الفرعية “تاريخ بروتوكول نقل النص التشعبي” في علامة تبويب الوكيل، سترى سجلًا لجميع طلبات بروتوكول نقل النص التشعبي التي أرسلها متصفحك وإذا نقرت على إحداها يمكنك رؤية الطلب الكامل وكذلك الاستجابة من الخادم.
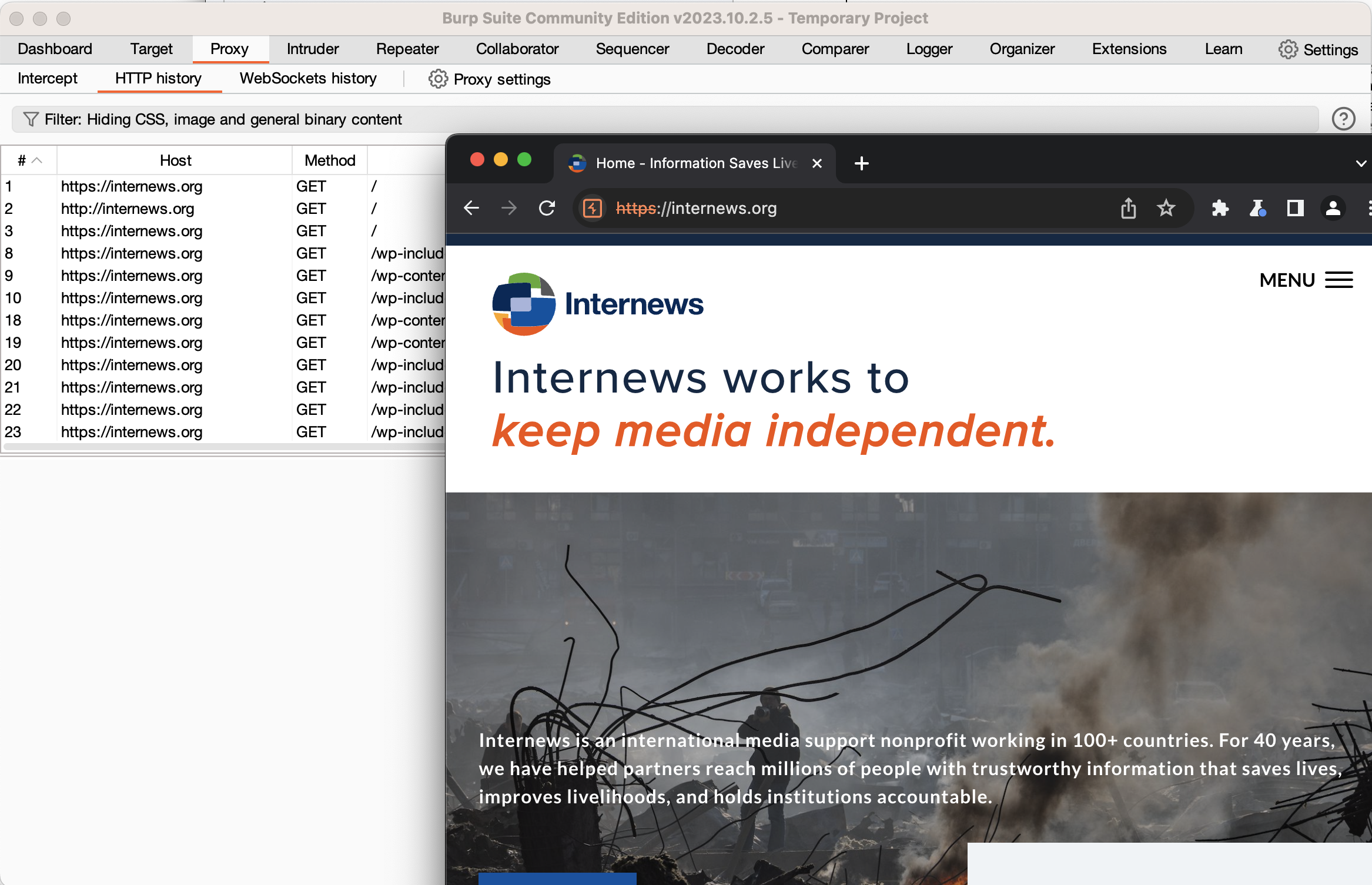
إذا كنت ترغب في تعديل طلب تم إرساله بالفعل، انقر بزر الماوس الأيمن على هذا الطلب وحدد “إرسال إلى المكرر (Send to Repeater)”. انتقل إلى علامة التبويب المكرر (Repeater) وسترى الطلب على اليسار. من المستحسن النقر على الفور على زر “إرسال” للحصول على استجابة طبيعية، ويمكنك بعها تعديل الطلب وإرساله بعد التعديل. يمكنك استخدام الزرين “<” و">" للاطلاع على الطلبات والاستجابات السابقة. يعد استخدام علامة تبويب المكرر أمرًا بالغ الأهمية عند إجراء تقييمات الأمان كما سيتضح من المواضيع الفرعية اللاحقة.
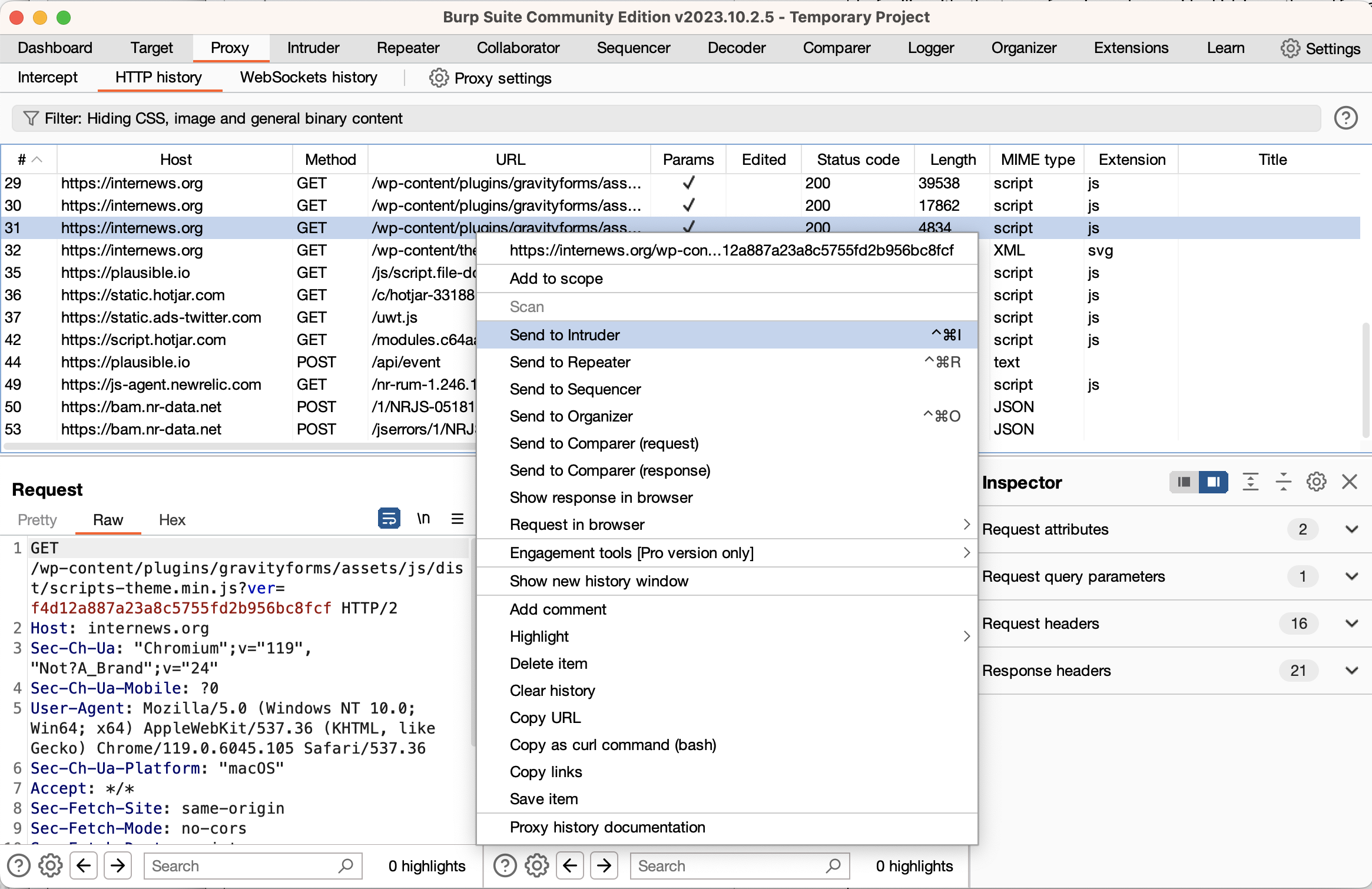
إحدى الميزات المهمة لواجهة المكرر هي ميزة “ترميز عنوان بروتوكول عنوان موقع ويب أثناء الكتابة”، مما سيؤدي تلقائيًا إلى ترميز الأحرف أثناء كتابتها مما يوفر لك العديد من الأخطاء والكثير من الوقت. حسب ما تقوم بتعديله ستضطر إما إلى تشغيل هذه الميزة أو إيقاف تشغيلها، ولتغيير الإعداد انقر بزر الماوس الأيمن على نافذة الطلب واختر عنصر القائمة.
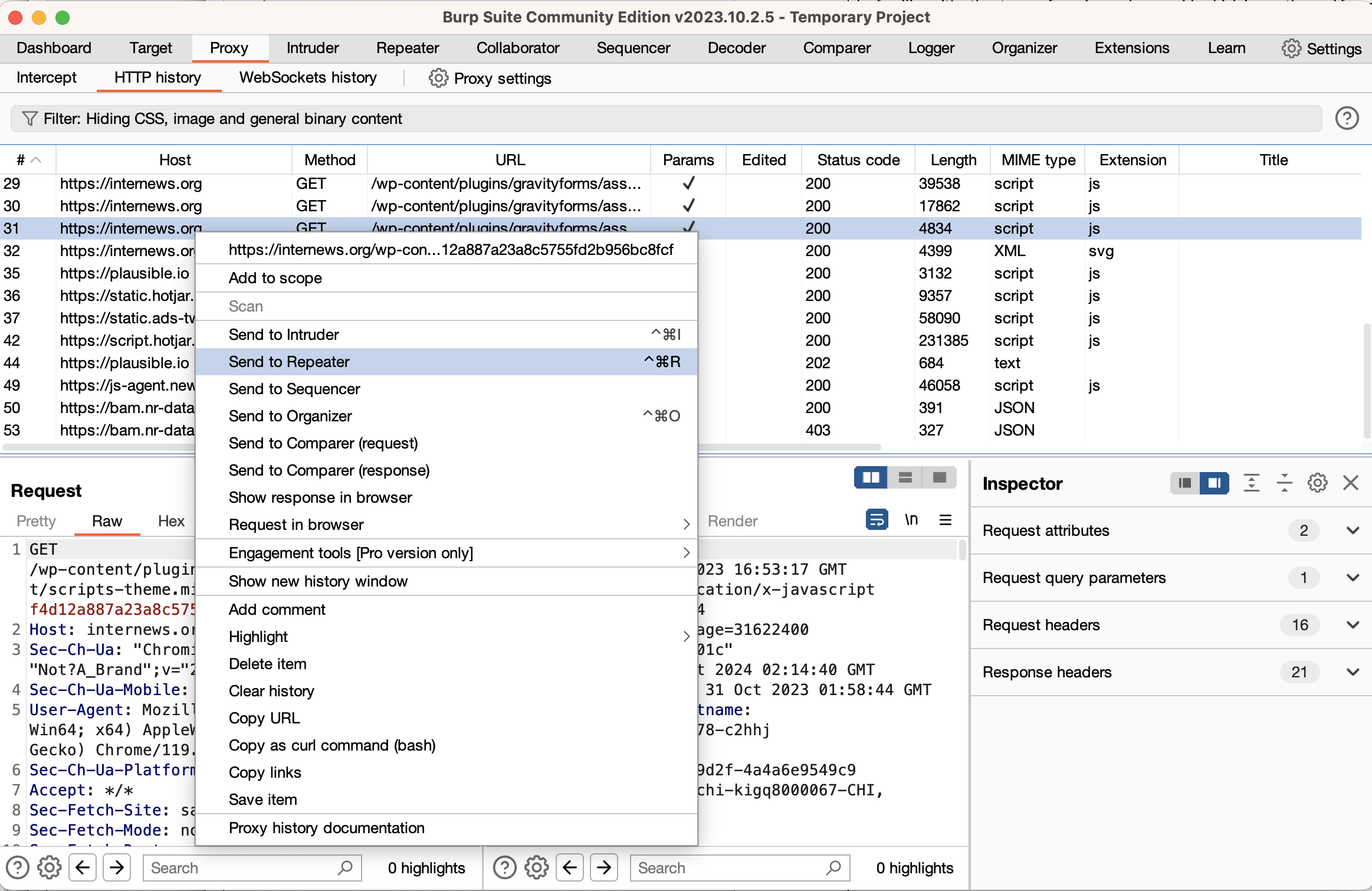
سيسمح ذلك لك بالبدء باستخدام بيرب سويت، ويكفي الإصدار المجتمعي المجاني لمسار التعلّم هذا، لكن معظم الأشخاص الذين يتقاضون أجورًا لقاء إجراء تقييمات أمنية لمواقع الويب يختارون الاشتراك بالإصدار الاحترافي. يتضمن كل من الإصدار المجاني والمدفوع عددًا كبيرًا من الميزات التي تم توثيقها على موقع بورت سويغر. ستتعمق أكثر في بيرب في معظم المواضيع الفرعية التالية (على الرغم من أنه يمكنك استخدام أي وكيل تريده إذا كنت تفضل ذلك).
بالنسبة لجميع المواضيع الفرعية حول فئات الثغرات، يمكن العثور على الغالبية العظمى للقراءة والتمارين في أكاديمية بورت سويغر، وهي موقع ويب مجاني يتضمن تمارين القراءة والمخابر التي تغطي الغالبية العظمى من مواضيع أمان الويب الشائعة. تُناقش هذه المواضيع في عدد من صفحات الويب التي تحتوي على روابط لتمارين المخابر ضمن الصفحات. ستحتاج إلى استخدام بيرب سويت كما هو موضح أعلاه لحل هذه المخابر. (يمكن حل معظم المخابر باستخدام أي عدد من وكلاء الاعتراض ولكن بعضها يتطلب بيرب على وجه التحديد.)
يخصص كل واحد من المواضيع الفرعية أدناه قسمًا للقراءة والمخابر من أكاديمية بورت سويغر، وخلال استكمال هذه المهام تأكد من مراجعة جميع الصفحات وإكمال جميع مختبرات المستوى “المتدرب”. يجب عليك أيضًا تجربة جميع مخابر مستوى “الممارس” ولكن حاول ألا تقضي وقتًا مفرطًا في أي مختبر واحد. في حال علقت في مخبر ممارس معين، ما عليك سوى المضي قدمًا والعودة إليه قبل إكمال تمرين التحقق من المهارات النهائي لمسار التعلّم.
ضمن موضوع البرمجة النصية عبر المواقع (XSS) على أكاديمية بورت سويغر، تأكد من مراجعة جميع المواضيع الفرعية، حيث تقع أقسام “ما هي البرمجة النصية عبر المواقع (XSS)” حتى “الاختبار” كلها على صفحة ويب واحدة، ولكن لكل موضوع فرعي صفحته الخاصة.

الموضوع الفرعي البرمجة النصية عبر المواقع المنعكسة على أكاديمية بورت سويغر، علمًا أن رابط المخبر موجود في أسفل لقطة الشاشة.
بعد الانتهاء من موضوع ما (مثل البرمجة النصية عبر المواقع)، تحقق مرة أخرى من إكمال المخبر عن طريق التحقق من رابط “عرض جميع مخابر الموضوع”، مما يتيح لك رؤية أي فحوصات مخبرية فاتتك.
** جربه بنفسك !!**
توجه إلى أكاديمية بورت سويغروسجّل حسابًا.
‼️ إذا كنت تشعر بأنك عالق في مخبر ما، يمكنك الاطلاع على عدد من أدلة التوجيه خطوة بخطوة والأدلة التوجيهيةعلى يوتيوب والمدونات، لكن لاحظ أنه من غير المرجح أن يكون اتباع أدلة التوجيه خطوة بخطوة مفيدًا جدًا لتعلمك. إذا وجدت نفسك بحاجة إلى عدة أدلة توجيه خطوة بخطوة كي تجتاز المخابر، فقد ترغب في العودة خطوة إلى الوراء وإعادة قراءة المواد ثم أعد محاولة اجتياز بعض المخابر التي أكملتها سابقًا بحذر مستخدمًا أدلة التوجيه خطوة بخطوة.
تُعدّ أداة زد أتاك بروكسي بديلًا مفتوح المصدر لبيرب سويت، وعلى الرغم من أنها ليست المفضلة بين المحترفين، إلا أنها تتمتع بميزة كونها مجانية وتتضمن أداة مسح لأمن تطبيقات الويب. على الرغم من أن واجهة المستخدم تختلف بين زد أتاك بروكسي وبيرب تبقى الميزات الأساسية ذاتها موجودة في كل منهما.
جربه بنفسك!
نزّل أداة زد أتاك بروكسي ثم انتقل إلى قسم التثبيت وواجهة مستخدم سطح المكتب وقسم استكشاف التطبيق يدويًا في دليل بدء تطبيق أداة زد أتاك بروكسي، حيث سنغطي أداة زد أتاك بروكسي بتعمّق أكبر في الموضوع الفرعي المتعلق بالأتمتة.
داكر هو نظام يسمح لك بتشغيل تطبيقات لينوكس في بيئة شبه مستقلة تسمى الحاويات، وعلى الرغم من أنها ليست آمنة مثل جهاز ظاهري كامل إلا أنها تتمتع بالخفة والمرونة. يتضمن داكر على نظامي تشغيل ويندوز وماك جهاز لينوكس ظاهري. ولأغراض مسار التعلّم هذا، سنستخدم داكر للسماح لك بتشغيل مواقع الويب الكاملة بسهولة على جهاز الكمبيوتر الخاص بك.
جربه بنفسك!
ثبّت داكر لسطح المكتب، علمًا أنك لن تحتاج إلى التسجيل للحصول على حساب أو الحصول على ترخيص تجاري لإكمال مسار التعلّم هذا. لاحظ أنه من المحتمل أنك أكملته كجزء من مسار تعلم أساسيات أمان تطبيقات الويب.
بينما يمكن للبشر أن يكونوا ماهرين جدًا في العثور على ثغرات حقن لغة الاستعلامات البنيوية (اختصارا بالانجليزية: إس كيو إل SQL)، فإن استغلال هذه الثغرات غالبًا ما يتطلب عملاً متكرراً للغاية. يعتبر إس كيو إل ماب أداة لحقن إس كيو إل تتفوق في عملية الاستغلال. تحتوي إس كيو إل ماب على برامج نصية تكتشف كيفية تعداد بنية قاعدة البيانات واستخراج المحتوى من قاعدة البيانات هذه باستخدام حقن لغة الاستعلامات البنيوية، وهو أمر مفيد جدًا لإظهار خطورة ثغرات حقن لغة الاستعلامات البنيوية ولإيجاد ثغرات أخرى تتعلق بتخزين البيانات.
** جربه بنفسك!** ثبّت إس كيو إل ماب. يمكنك إما تنزيله (يعمل على بايثون) أو استخدام حزمة كالي.
ضمن مجتمعات الصحافة المستقلة والمجتمع المدني، تستخدم العديد من وسائل الإعلام ووردبريس (WordPress) لمشاركة محتواها، ويُعدّ ووردبريس برنامجًا معقدًا يحتوي على العديد من المكونات الإضافية وخيارات التكوين التي يمكن أن يكون لها تأثيرات أمان كبيرة. كجزء من الموضوع الفرعي للأتمتة، سنستخدم أداة مفتوحة المصدر تسمى دبليو بي سكان للعثور على ثغرات الأمنية في موقع ووردبريس.
جربه بنفسك!
ثبّت واجهة سطر الأوامر دبليو بي سكان، ولاحظ أنه يمكن القيام بذلك من المصدر أو من مدير الحزم (مثل هومبرو (homebrew) أو روبيجمز (rubygems)) أو كحاوية داكر أو باستخدام الإصدار المضمّن في العديد من توزيعات الجهاز الظاهري لاختبار الاختراق مثل كالي لينوكس. الأمر متروك لك وبإمكانك الاختيار، علمًا أننا سنغطي دبليو بي سكان في الموضوع الفرعي المتعلق بالأتمتة.
تأكد من تثبيت وإعداد الأدوات التالية التي أدرجناها أيضًا أعلاه:
لا يوجد اختبار مهارة
PortSwigger Academy
FreeCollection of explainers and labs on web application security.
What is a reverse proxy?
FreeOverview of reverse proxy compared to forward proxy.
Commercial proxies and content delivery networks
VariedFastly, Cloudflare, Amazon CloudFront.
Burp Suite
Community version is free, Pro edition costs $449 per userPopular web security testing tool.
Docker Desktop
FreeTool to install containers containing executable applications.
تهانينا على إنهائك الوحدة 1!
حدد خانة الاختيار لتأكيد إكمالك والمتابعة إلى الوحدة التالية.
تحديد الوحدة الحالية على أنها مكتملة وحفظ التقدم للمستخدم.
لقد أكملت جميع الوحدات في مسار التعلم هذا.