Module 10
Capture-the-flag exercise
Last updated on: 17 December 2024
Edit this page on GitHubModule 10
Last updated on: 17 December 2024
Edit this page on GitHubWe have also designed a capture-the-flag exercise in which learners can analyze a phishing email and the infrastructure it links to. The exercise can be used as an additional practice or skill verification exercise, and can be found below.
You are sitting in the bustling Press newsroom where you are working as an IT admin, sitting totally focused on your duties surrounded by glowing monitors. Your colleague Alia from Accounting rushes over with a concerned look on their face, who lets you know they forwarded an email claiming to be from PayPal which urges them to take immediate action due to suspicious account activity. The Press organization relies on PayPal for processing subscription payments. Your interest is instantly piqued as you recognize the potential of a malicious attack, and you get started on an investigation.
This activity utilizes a sample email and landing page needed for this activity. Download the files here: CTF Materials
There are multiple ways to view what the email would look like to the recipient. The most straightforward way is to open the file in a mail client, which is what we have done in the below examples. However in the context of a targeted threat this can be a bad idea, in case the file contains scripts which can exploit email clients, collect information about the device, or load external resources (like /media/uploads/tracking pixels) which disclose your IP to the attacker. In the case of this walkthrough it is safe to open the EML in your email client, however for live work consider some alternatives:
In this walkthrough we will just open the email (paypal.eml) in an email program
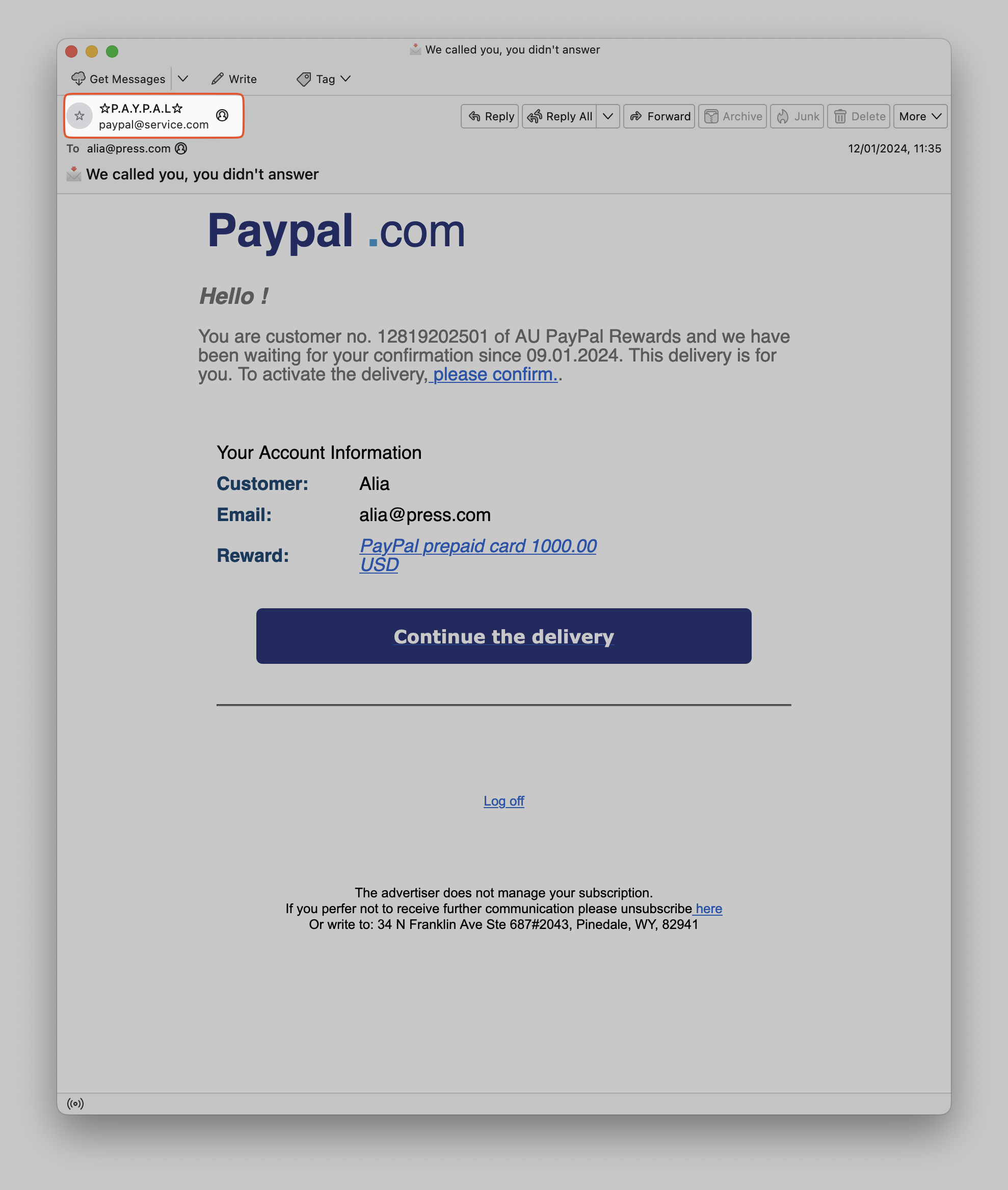
As we look into the email, we see the visible sender email address
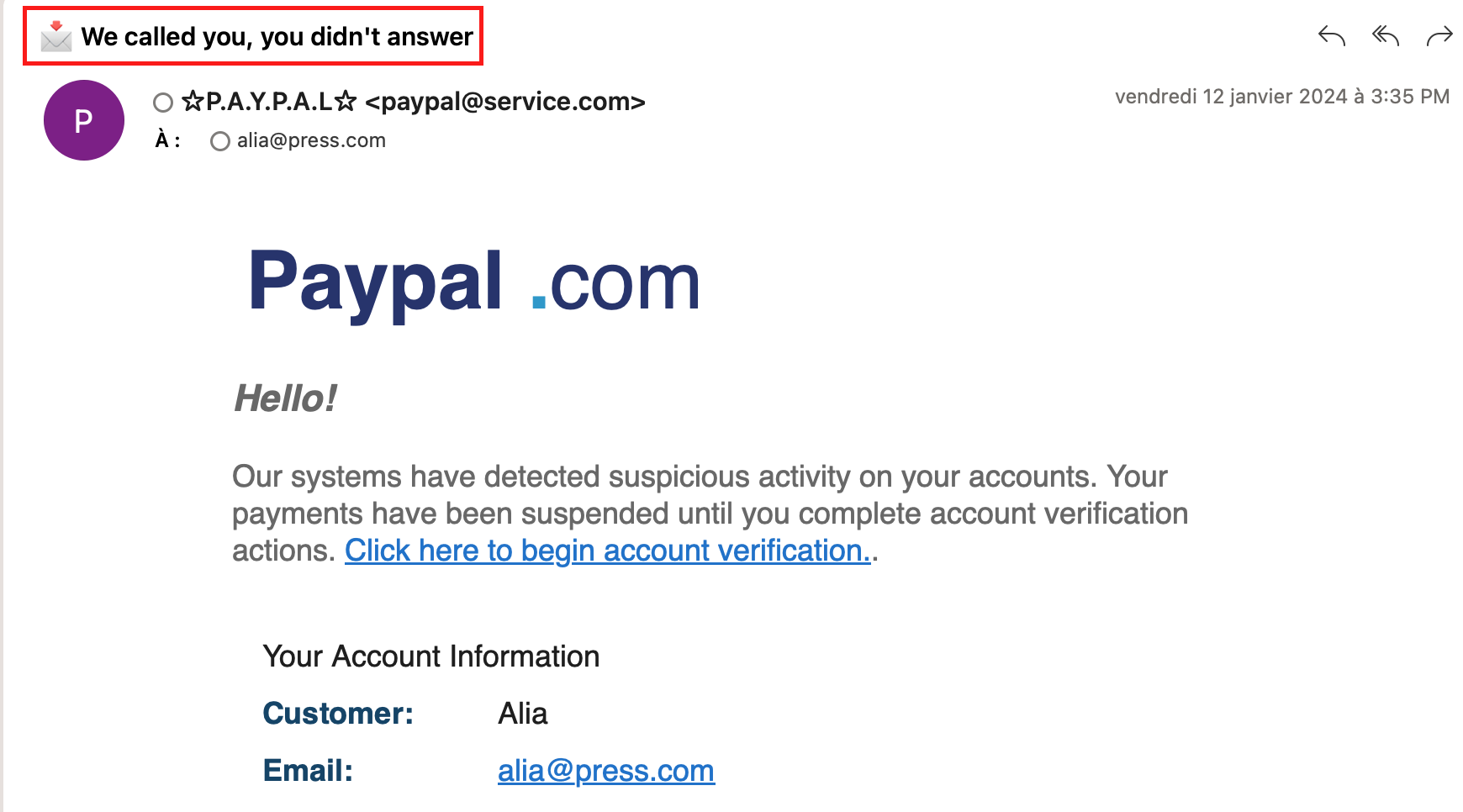
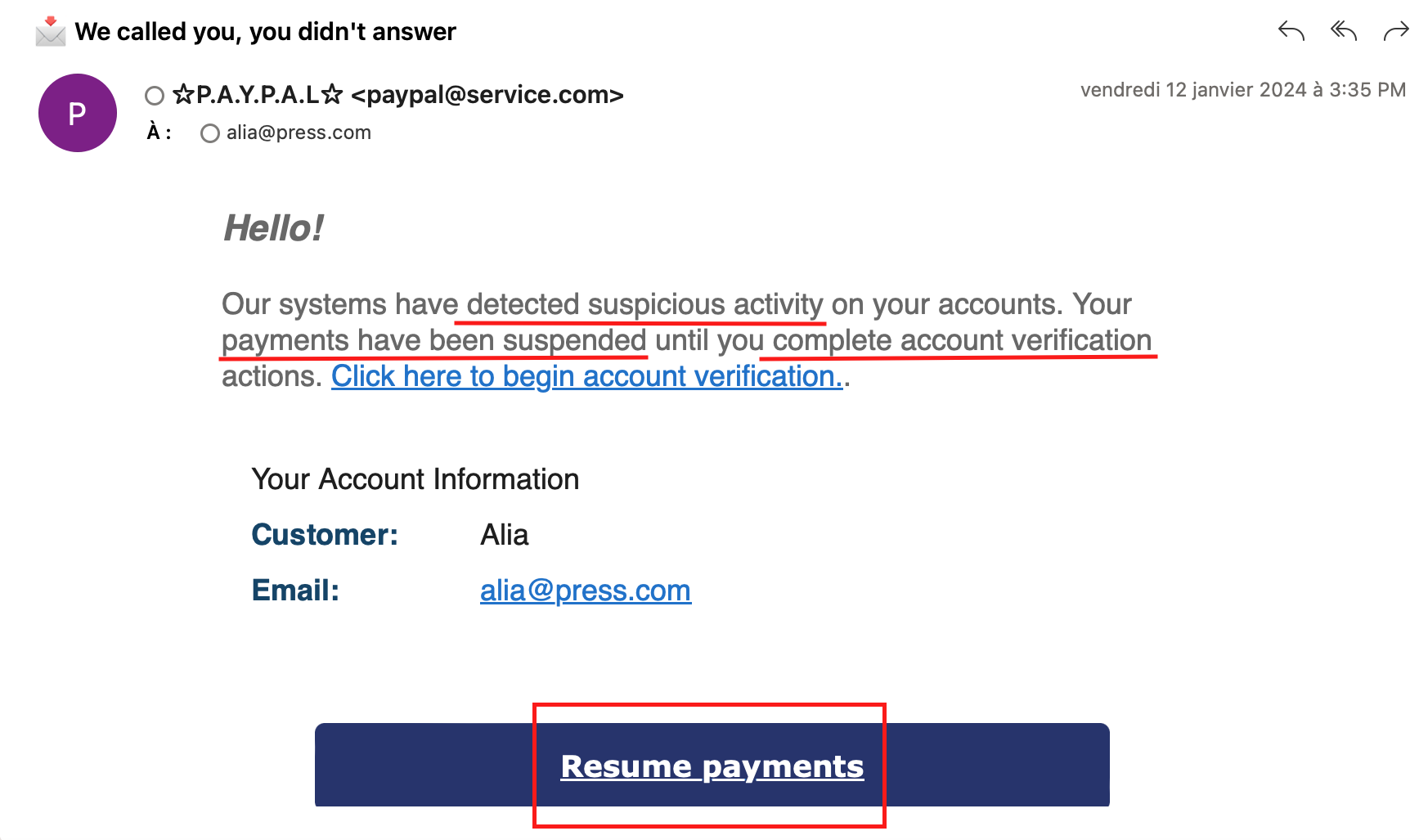
Here are some key trigger points to watch out for in a phishing email:
You can defang a link in a text editor. Here we will use CyberChef to defang the URL as we will use CyberChef for other steps as well. CyberChef is a web application with a huge number of functions which can help you with analyzing security-related data. Here’s a very brief introduction to its layout and functions.
As part of this exercise, play around with CyberChef and defang the “please confirm” link from the attached email.
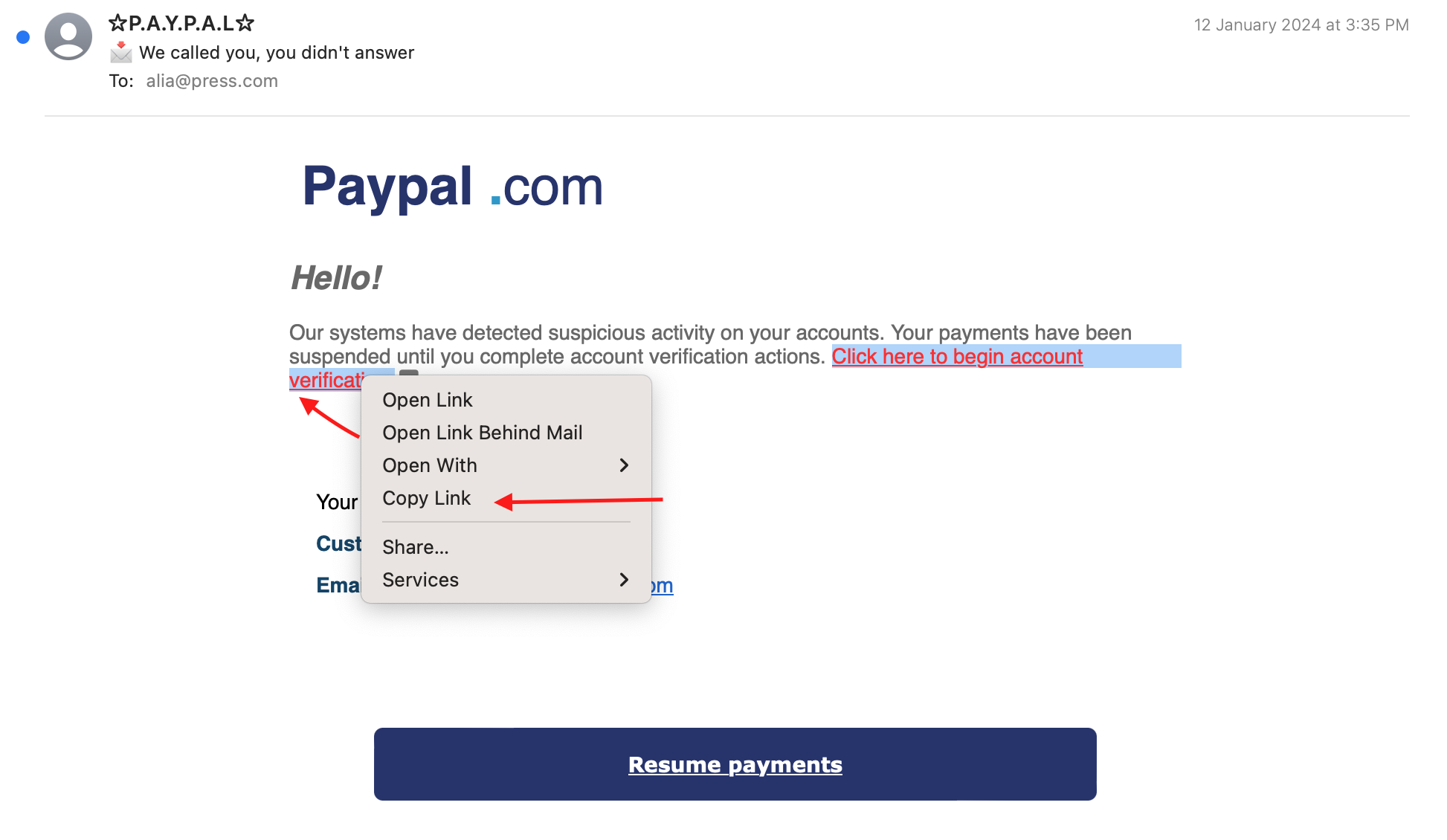 First, we copy the hyperlink from the email.
First, we copy the hyperlink from the email.
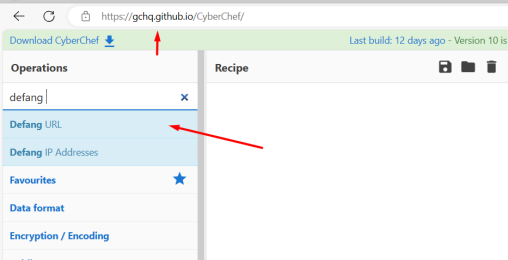 Then, we take the “Defang URL” input from CyberChef and drag it into the “Recipe” section
Then, we take the “Defang URL” input from CyberChef and drag it into the “Recipe” section
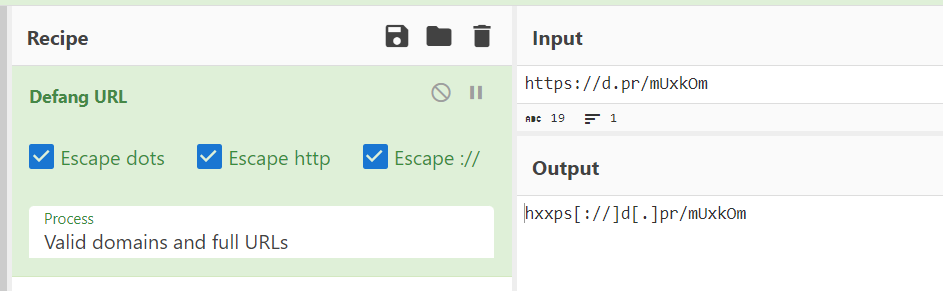
Once we’ve pasted the URL into the input section in CyberChef, it will automatically output a defanged version thereof.
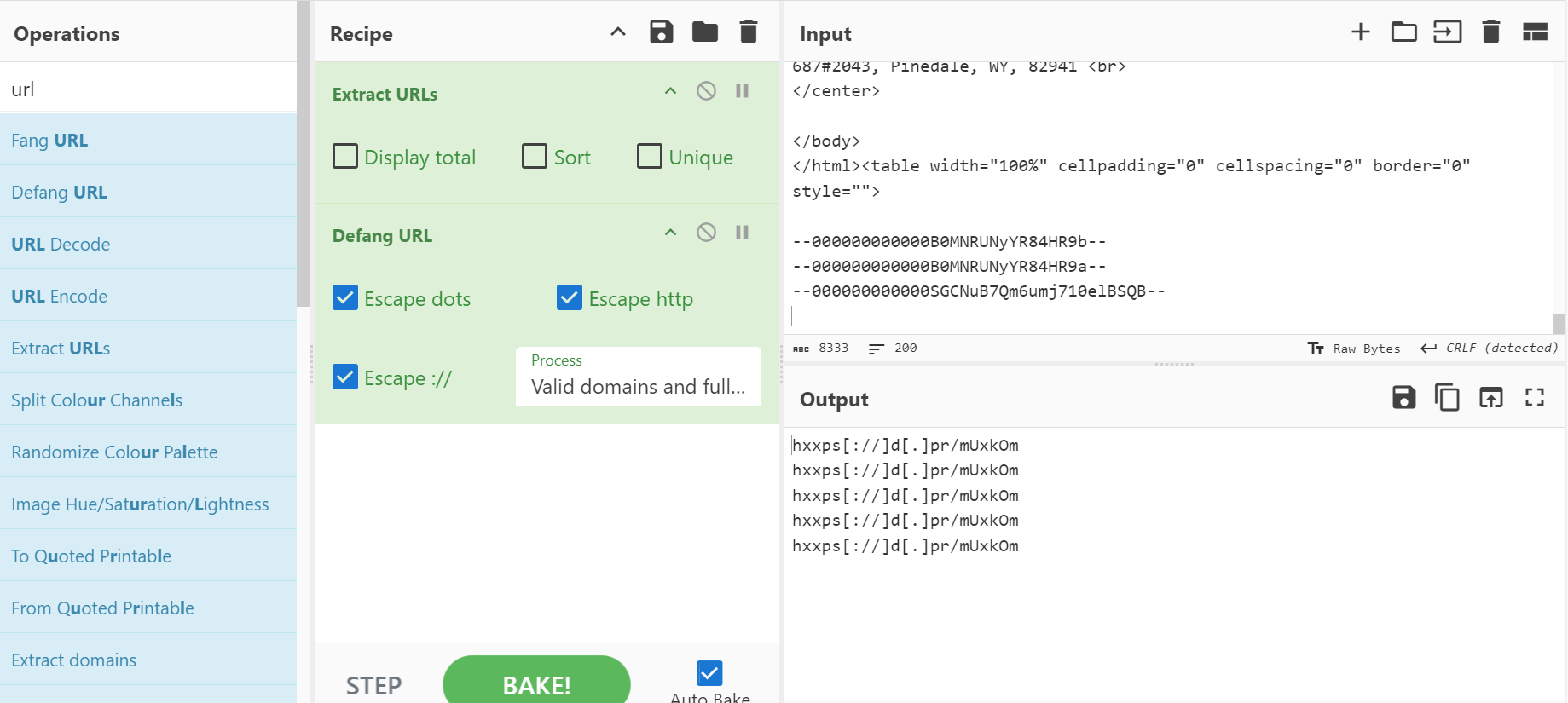
You can use a ‘recipe’ – or a series of connected steps –in CyberChef to carry out a more complex analysis. To obtain and defang all the URLs in the message, all you need to do is run a recipe with the “extract URLs” and “defang URLs” workflows and paste the full content of the email (copied from a plain text editor) as input. If you were to tick the “unique” checkbox under “extract URLs”, you will see that the results will differ from those from the screenshot, and it will only output a single URL, the same one you defanged above. The fact that there is just one URL, repeated many times, within the email is great news for us–it will make our analysis much more straightforward. \
For the next few questions, we will use VirusTotal. It’s an online service that acts like a security scanner for suspicious files and URLs. Think of it as a digital inspector. You can upload a file or provide a URL, and VirusTotal scans it with antivirus engines and website checkers from dozens of different security companies. It also performs some additional analysis. This gives you a quick overview of whether the file or website is likely to be malicious. It’s a valuable tool to help you identify potential threats before you open an attachment or click on a link. It also contains metadata about files which may be helpful. Here we will use the entry history to find out when a malicious indicator was first observed.
Paste the URL from question 4 into VirusTotal (this time, you need to paste the full URL, not the defanged version). Go to “details” tab and look at the URL capture history.
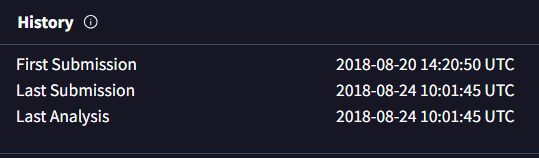
Also looking through the “details” tab in VirusTotal, look up the serving IP address.
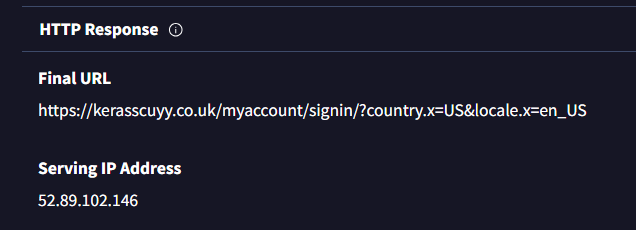
Here we use a whois website to extract it
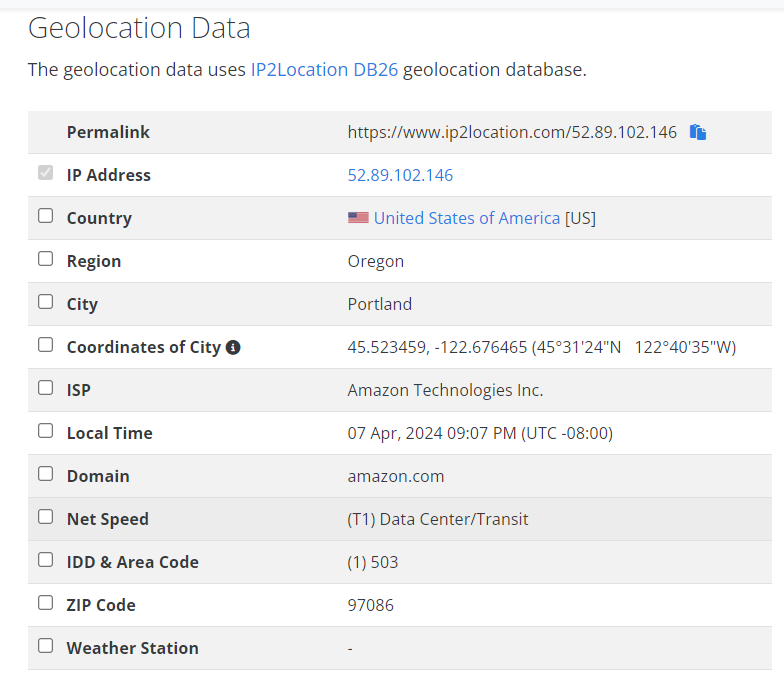
IP addresses are loosely tied to geographical locations, such as cities or districts. There are many online services where you can input an IP address and learn more about where it’s most likely located. While this type of check is not perfect and can sometimes make mistakes, it can nonetheless be an important part of malicious infrastructure investigations.
It’s worth comparing the information you receive from a whois lookup with that you receive from IP location searches. You might learn that the IP address you are trying to investigate belongs to a VPN provider or a big tech company such as Google–if this is the case, then you will not learn much from those investigations; the IP location will likely correspond to one of those companies’ server farms and might have little to do with the location of the person or entity you’re trying to investigate.
First, open the email using a plain text editor of your choice and copy its content. Then, paste them into the MxToolbox’s “Analyze Headers” tool
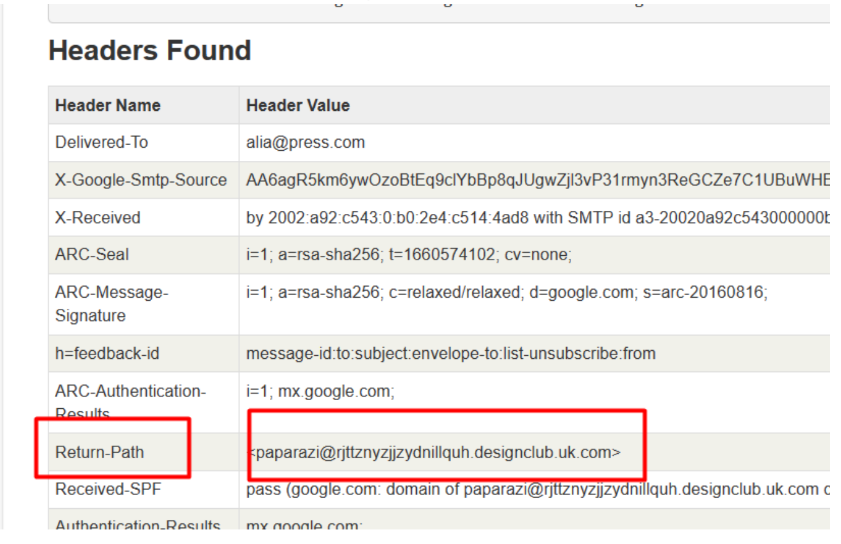
Once you press “Analyze Header”, you can see the return path
Go to the file mx-toolbox-header-analysis.pdf, look into the relay information section.
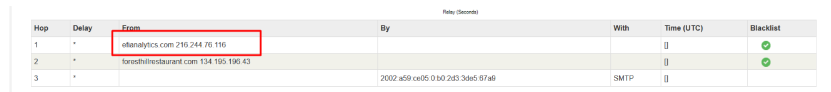 The address of the mail server
The address of the mail server
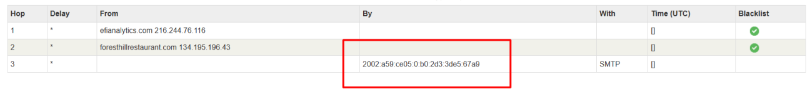
First hop: efianalytics.com 216.244.76.116
SMTP: 2002:a59:ce05:0:b0:2d3:3de5:67a9
In this exercise, you will encounter a string of text encoded in Base64. Base64 is a technique for transforming text that has many purposes, but in this case aims to obfuscate a string of text: the string is still there, it’s just saved in a way that cannot be easily spotted by the human eye or by a simple text search. If this is the first time in your work you’ve encountered Base64, it’s worth reading a little more about it and other obfuscation formats. Malware authors like to obfuscate some text strings within their programs using a technique such as Base64 in order to make it more difficult to analyze.
CyberChef can encode and decode Base64 text.
We open once again the code attached of the phishing page (.html)
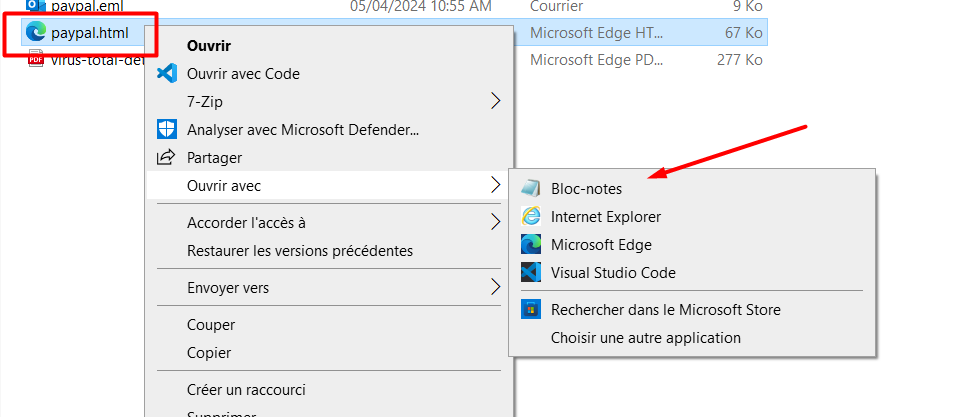
we search for the victimID in the source code
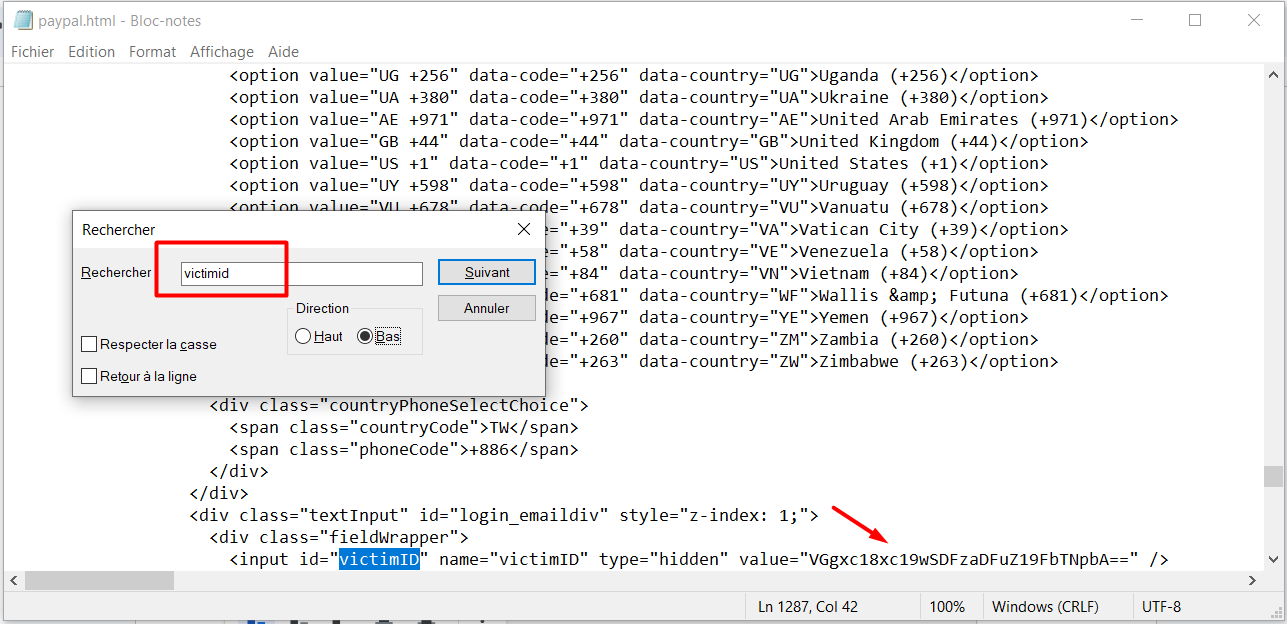
Then we can paste the value we discovered into CyberChef. The tool has a magic wand feature which automatically detects and converts encoding–we could use that!
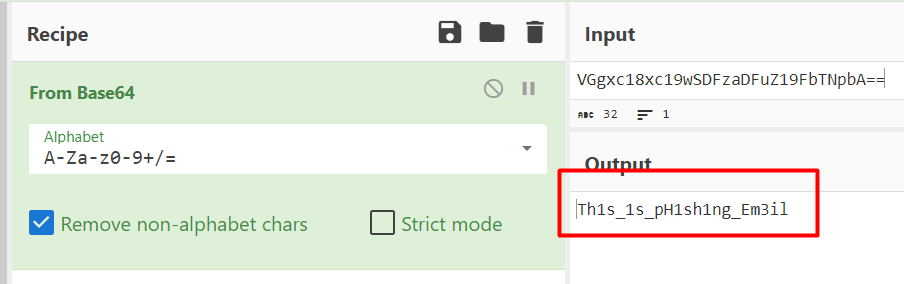
Yay! The magic wand detected that the input is encoded with Base64 and decoded it automatically, giving us the answer!
Access Now helpline community documentation for responding to suspicious/phishing emails
FreeClient Receives a Suspicious/Phishing Email
List of all DNS record types
FreeIncludes (almost?) all DNS record types.
Amnesty reports on phishing campaigns
FreeA list of examples of how a targeted phishing campaign against human right defenders, activists and journalists looks
Congratulations on finishing Module 10!
Mark the checkbox to confirm your completion and continue to the next module.
Marks the current module as completed and saves the progress for the user.
You've completed all modules in this learning path.